TunnelBear Review (2024)
TunnelBear is outstanding because of its user-friendly app and bear-themed terminology. This fun service is easy to use and helps people understand how VPNs work through its animation. While the functionality of the app is great and is a great option for first-time VPN users. If you have no idea what a VPN is, read this review to get a detailed explanation.
What we like
- Amazing app animation
- Fun bear-based terminology
- Works in China
- Public WiFi hotspot protection
- Free version
What we don't like
- Doesn’t install on routers
- No VPN app for Linux or Chrome OS
- No longer offers a browser extension for Opera
- Can’t get into Disney+, ABC, or the ITV Hub
Features
| TunnelBear Features | |
|---|---|
| Rating: | 4/5 |
| Price: | $3.33 – $9.99 per month |
| Refund period: | 0 days |
| Based in which country: | Canada |
| # devices per license: | 5 |
| # servers: | Unknown |
| Server locations: | One location each in 48 countries including USA, Canada, UK, Australia, New Zealand, Japan, France, and Germany |
| Streaming sites unblocked: | Netflix, NBC, BBC iPlayer, and Channel 4 |
| Supports torrenting: | Yes |
| Does VPN keep logs: | No |
| 24/7 customer support: | No |
| Website: | https://www.tunnelbear.com |
TunnelBear was created by Ryan Dochuk and Daniel Kaldor in 2011. The company has always been based in Toronto, Canada, but there were major changes with this VPN provider in 2018 when it was bought by McAfee.
The VPN service still has the sense of fun that its founders instilled in the business, but Dochuk and Kaldor are no longer involved with the company. After five years in executive positions with McAfee, Dochuk left the company in March 2022 to start up OnlyForward, an app development company. Daniel Kaldor spent three years as a Senior Principal Engineer at McAfee and has been running Neural Squared, a British machine learning developer since June 2021.
Despite the very strong technical skills of its founders, TunnelBear is much stronger on branding that the technical aspects of a VPN service. The service doesn’t overburden its potential customers with the technical details of the VPN service. This system is for people who want privacy protection and are not that bothered about how that’s done.
There is no way to set up the TunnelBear service on routers or smart TVs and speeds are not that great. However, 200,000 people download the TunnelBear app every month, so the service is doing well catering to people who love its bear animation.
Privacy and security
Cybersecurity has many avenues. For example, defending a system from attack requires the type of software that McAfee provides. Data security, in movement and at rest, relies on the use of encryption.
Privacy is a slightly different matter from security. Although preventing outsiders from stealing information is important, the main purpose of internet privacy is to prevent organizations from tracking the activity of users.
Not all of the components in a privacy system are computer-based. Some of them are procedural and others are legal measures.
Legal protection
Security and privacy systems won’t protect you from government agencies if the company running your protection system is working with the government. This situation does happen, particularly in Five Eye spy ring nations, of which Canada is one. The corporate ownership of TunnelBear makes the company even more susceptible to US government pressure.
The matter of copyright protection – is of particular interest who those who want to use torrenting networks or dodge the location restrictions on video streaming services. McAfee is equally vulnerable to pressure.
When you read about VPN providers, you will notice that issues about logging are considered to be extremely important. This is because, in some countries in the world, VPN services are expected to record which customers were using the system at what time and which fake IP addresses were given to them for the session. No one does anything with these logs. However, they are available to copyright lawyers who can get a court order for them.
In Canada, internet service providers (ISPs) retain all activity data on their customers for 6 months, which can be extended to 12 months with a court order. These obligations do not apply to VPNs. However, a VPN provider can be forced to start logging a specific user’s activities as part of an investigation.
Canada’s Copyright Modernization Act allows copyright holders compensation from people who get illegal copies of entertainment or illegally watch streams. This payment is capped at $5,000 per infringement.
Although every VPN provider says it doesn’t log activity, many of them are lying. TunnelBear has a no logging policy. It claims that its confidentiality processes are confirmed by an annual security audit by Cure53. However, this is a vulnerability assessment that performs penetration testing on the servers that run the VPN. That declaration of security doesn’t guarantee that TunnelBear doesn’t keep logs.
Network address translation
There are two purposes of a VPN, the first is to hide your online activity, and the second is to hide your internet identity. These tasks are performed in two phases. All of the internet traffic of a TunnelBear VPN client gets diverted through a TunnelBear server. The connection to the server is protected with encryption, and the activity that is forwarded out of the server is protected by address substitution.
Network Address Translation (NAT) is the mechanism that the TunnelBear VPN uses to hide the identities of its clients. Every device on the internet needs a unique identifier called an IP address. In order to enforce uniqueness, the allocation of IP addresses is centrally controlled. The addresses are released in blocks to regional authorities, who then sell them in bulk to registrars.
The eventual buyer of each address is registered in order to block its reuse, and the registration process identifies the physical location of the buyer. The location information of each IP address is publicly available, and it is this data that tells Web servers where a request for content comes from. This enables a video streaming service to alter the content that it delivers or block access completely. Other sites, such as online gambling, gaming, and news sites, use the same reference system to block access or modify content.
The VPN system bypasses regional restrictions because you choose a server in a specific location before you connect. Once the VPN session is active, all of your traffic will appear to be from that location. Data passes over the internet in packets. The packet has a header on it, which include the source and destination addresses. It is the source address that tells Web servers where you are. The VPN server puts its own IP address in that field.
When the code for a website is returned, it goes to the VPN server. TunnelBear operates a pool of IP addresses for each server. One of these is allocated to a customer at the beginning of the session. There might be many customers channeling traffic through the same server at the same time, and the server allocates a different temporary address to each. This is the network address translation system, and looking at the cross-reference between client IP addresses and their substitutes enables TunnelBear to forward replies back to the right customer.
Does TunnelBear keep logs?
Once a customer turns the VPN service off, the allocated IP address goes back into the server’s address pool for reuse. The entry in the NAT table is deleted. A VPN that keeps activity records stores these mappings on a disk for a long time after the session ends. There isn’t any business advantage to TunnelBear in storing these mappings. This lack of incentive is the main reason that analysts believe Tunnel Bear’s no logs policy statement – keeping logs without legal compulsion just incurs a storage cost for no business benefit.
TunnelBear VPN protocols
Internet and network-based systems need to interact with each other. It isn’t possible for one company to write every piece of network software in the world, so the industry works to a set of guidelines, which ensures that software written by different people will be compatible. These guidelines are called protocols.
There are a number of protocols that were specifically written to provide VPN services. TunnelBear offers four of these in its apps:
- OpenVPN – This is the most widely-used protocol used for VPNs. It is an open-source system, and the core of its connection processes is provided by a library called OpenSSL.
- WireGuard –This is a new VPN protocol that provides the same work as OpenVPN but in less code. This is a very highly regarded system, and many VPN providers are adding it to their apps. However, as it is new, the protocol hasn’t been proven by extensive usage like OpenVPN.
- IPsec – This is a very efficient VPN protocol that was invented by Cisco Systems. It operates right down at the network level and doesn’t get slowed down by high-level session management procedures. This makes the service good for mobile devices because it places less load on the battery.
- IKEv2 –IPsec’s lack of session-level functions means that it isn’t able to manage encryption key exchange. This task is provided by IKEv2, so these two protocols are always used together.
You don’t get all of these options in all apps. In fact, in
- Windows – OpenVPN, WireGuard, IKEv2/IPsec
- macOS – OpenVPN
- Android – OpenVPN
- iOS – OpenVPN and IKEv2/IPsec
TCP Override
TCP is the Transmission Control Protocol. This is a Transport Layer protocol that deals with session management. When any type of connection is made across a network or the internet, there are a number of factors that need to be negotiated. These include authentication procedures and session setting such as the encryption cipher to use and the key that will be used with it. While the session is underway, TCP periodically sends an ACK packet to which the other side responds, ensuring that both sides in a connection are still listening. It also ensures that lost packets are replaced and that packets arriving out of sequence are put into the proper order.
TCP is a great service, and it dominated network and internet management for decades until video streaming and internet telephony came along. One packet in a stream represents just a split-second of sound or video, and its loss is slightly annoying. However, the full package of TCP services really slows down a connection to the point that there will be long gaps on a VoIP call and pauses for buffering in video streams.
Interactive systems don’t work well with TCP. They are in luck. Right from the start of the internet, the designers provided an alternative to TCP, which is called the User Datagram Protocol (UDP). This set of guidelines does just about nothing, which means that it doesn’t slow transmissions.
The TunnelBear app has a setting in its VPN protocol selection screen called TCP Override. This only applies to OpenVPN connections. This is because WireGuard and IKEv2/IPsec only work with UDP, whereas OpenVPN can use either UDP or TCP.
The OpenVPN implementation in TunnelBear defaults to UDP. You can make it use TCP instead if you turn the TCP Override option on. This option is only available in the Windows and macOS apps.
TunnelBear client connections
No one gets internet access without going through an internet service provider (ISP). This means that all of your traffic passes through the computers of an ISP, and this is where mandatory activity logging occurs in most countries.
The intrusion on online privacy by ISPs is legal, but it can be avoided. VPNs, including TunnelBear, block the ISP’s intrusion by diverting all traffic to its own servers. The driver for this redirection is the TunnelBear app. This is actually a VPN client that negotiates a secure connection with the chosen VPN server. This includes an agreement on which encryption system to use for the connection.
Once the secure connection has been established, all traffic from the customer’s computer gets processed by the TunnelBear app so that it is encrypted on its journey. This encryption is performed in such a way that ISPs can’t see where the traffic is really going. In VPN technology, this encrypted connection is called a “tunnel.” That’s where the TunnelBear name comes from.
The VPN server is not the ultimate destination of that traffic. The real destination’s IP address is written into the IP header of the original packet sent by the customer’s computer. However, the TunnelBear app completely encrypts that packet, including the header, which contains the destination address.
A packet cannot travel across the internet if the header is encrypted because that blocks routers from reading the destination IP address. So, the client places that encrypted packet inside another packet and addresses the outer packet to the VPN server. This process is called “encapsulation,” and it guarantees that the IP address can never see the real correspondents of the client’s traffic.
By cloaking the true destination of all online activity, the VPN provides privacy. The encryption process also adds security because no snooper can read packets in transit.
TunnelBear VPN encryption
TunnelBear uses two phases of encryption. First, it uses a public key encryption system called RSA. This is a session establishment process that is dictated by SSL. All secure Web traffic that is transported through HTTP is protected by SSL.
SSL stands for Secure Socket Layer, but it is a misnomer. The secure Socket Layer was discovered to have security weaknesses, so it was replaced by Transport Layer Security (TLS). So, although the security process is called TLS, the total package is still called SSL – it’s a quirk of networking technology.
RSA isn’t used to encrypt packets. The main encryption system for the connection is called the Advanced Encryption Standard (AES). This cipher is a symmetric encryption system, which means that both sides need the same key to encrypt and decrypt a text. This presents a problem because, under this scenario, one side would need to send the key to the other over an unencrypted link.
RSA steps in for session establishment because, as a public key encryption system, it uses a key pair, with one key for encryption and the other for decryption. You cannot guess the decryption key if you know the encryption key, and you cannot decrypt a test with the encryption key. Thus, it is safe to publish the encryption key as long as the decryption key is kept secret.
The encryption key is published on an SSL certificate, which is held by a third-party certificate authority. When establishing a connection to the VPN server, the TunnelBear app gets the SSL certificate for that server and then sends a challenge encrypted with RSA, using the key on the certificate. If the reply solves the challenge, the server has proved its identity because an interloper wouldn’t possess the private key that corresponds to the public key from the certificate. The server also gets the client’s certificate and uses that to protect replies. Once both sides are authenticated, the server sends the AES key to the TunnelBear app, and the tunnel can be established.
The strength of a VPN cipher is dictated by the length of its key. This is because hackers can crack encryption through trial and error, trying different values for the key until the encrypted text becomes readable. This is called a brute force attack. Thus, an encryption key needs to be long enough that it would take too long to crack.
TunnelBear uses a 2048-bit key for its RSA encryption. This seems to be very long. However, public key systems need much longer keys in order to be uncrackable. It is known that RSA with a 1024-bit key can be cracked. So, a 2048 bit is the next victim on the block, and you can bet that hackers and the technologists of repressive governments are working on RSA-2048 right now.
Symmetric key systems need much shorter keys. TunnelBear uses a 256-bit key for its AES implementation (AES-256). This is the strongest key available and is very good.
For comparison, all of the leading VPNs use AES-256 encryption. The difference between VPN providers lies in the length of the RSA key that they use. Almost all of the paid VPNs use a least a 2048-bit key. Surfshark, Hotspot Shield, and IPVanish use a 2048-bit key. ExpressVPN, NordVPN, and CyberGhost use a 4098-bit key.
TunnelBear Private DNS
The Web addresses that you type into your browser mean nothing to the routers on the internet – they only deal with IP addresses. Before your computer can send a request for a Web page, it first has to find out the IP address of the Web server that can deliver it.
The cross-reference between Web addresses and IP addresses is called the Domain Name Systems (DNS). Your ISP will log all DNS queries, and that lets them record all of the websites that you visit, even if your computer’s requests for those pages go down the VPN tunnel.
Your computer’s default location for DNS information is the DNS resolver, and that responsibility gives the ISP the opportunity to block access to many websites. This is achieved by returning a false IP address that points to an error page instead of to the actual Web server needed for the site.
TunnelBear provides its own DNS resolver, and once a VPN connection has been established, all of your computer’s DNS queries go down the tunnel to the TunnelBear DNS.
TunnelBear VPN app security
There are a number of optional features in the #tunnelBear app that can enhance security.
- VigilantBear – This is what is known as a kill switch. It blocks all traffic from the device from getting onto the internet without an active tunnel in place. This measure prevents an incident that is known as an IP leak – unprotected traffic goes onto the internet without the user realizing it.
- GhostBear – This is an obfuscation option. It will slow down traffic, but it is very good at making VPN traffic look like regular secured HTTPS traffic. The method is very similar to a VPN strategy that is called Stunnel, and it confounds the Web access controls in China.
- Unsecured network detection – This setting generates an alert if the device is about to connect to a network with poor or no security. This is particularly useful for WiFi networks. The user still has to make the decision on whether to open a VPN connection.
TunnelBear VPN split tunneling
You’ve probably got the message that you should get a VPN, and once you have installed one, you should keep it turned on all the time to stop your online activity from being logged or controlled. However, there might be types of traffic that don’t need to be private, and you don’t care whether your ISP logs them.
VPNs perform a lot of work on incoming and outgoing traffic, and that is going to show down transmissions. So, if you have activities that are completely innocuous and you don’t mind them being logged, you can set up the TunnelBear service so that those applications always run outside of the tunnel, while torrenting or streaming from another country will always be performed within the protection of the VPN. This situation is called slit tunneling.
TunnelBear offers split tunneling in its mobile apps. It is called SplitBear and is available from the Options menu in the app. In order to activate it, turn the slider at the top of the screen to On and then check the boxes for all of the apps that you don’t want to be protected by the VPN.

Browser extension
The desktop apps don’t have the SplitBear feature. However, TunnelBear produces browser extensions for Chrome and Firefox (given how useful and ubiquitous chrome extensions are). If you turn the VPN on in the browser instead of using the desktop app, only browser traffic will travel down the tunnel, and all other applications will connect outside the VPN system.
Website blocking
A big reason that many people subscribe to VPNs is to get around the location restrictions imposed by video streaming services. VPNs can help you seem to be in the right country to get access. However, it can’t help you avoid paying for the service. So, if a video platform charges, such as Netflix or Amazon Prime Video, you still need a subscription with that service in order to get access.
We tested the TunnelBear VPN service with a number of well-known streaming services, and here are the results:
| Service | Test |
|---|---|
| Netflix | Yes for the USA, the UK, Germany, and France. No for Japan |
| Disney+ | No (tried the UK, France, the USA, Germany, and Japan) |
| BBC iPlayer | Yes |
| ITV Hub | No |
| Channel 4 | Yes |
| ABC | No |
| NBC | Yes |
In the cases where the VPN gained access, playback occurred smoothly without pauses for buffering, which shows that TunnelBear VPN is fast enough for streaming.
Pricing
Apart from the Free plan, TunnelBear offers two packages. These are the Unlimited plan for private use and the Teams plan for businesses. You can have multiple users with the Unlimited plan, but they all have to be family members living at the same address. The Teams plan has a central administrator’s console, which isn’t included with the Unlimited plan.
Each plan is offered in three subscription periods. Longer periods work out cheaper per month, but you have to pay for the entire period upfront. There is no free trial or money-back guarantee because TunnelBear expects buyers to use the Free plan to test the service before buying.
The prices for the Unlimited plan are:
- One-month plan — $9.99 per month
- One-year plan — $59.88 ($4.99 per month)
- Three-year plan — $120.00 ($3.33 per month)
You can pay for your subscription with a credit card (Visa, Mastercard, or American Express). It isn’t possible to pay through PayPal or with Bitcoin.
Access the TunnelBear VPN Free Version
TunnelBear’s free app has all of the functionality of the paid service, except that this system has a data throughput limit of 500 MB per month. This means you won’t be able to use it for long for torrenting, online gaming, or video streaming. However, it is a handy tool to have, and if you get to enjoy using the service, you can upgrade for unlimited data. The bandwidth, which is the capacity of an internet connection, is the same for both free and paid services.
As TunnelBear doesn’t offer a free trial, the free plan is you best way to test the VPN service without any financial obligation.
To get the free VPN app for Windows, go to the TunnelBear Download page. This will download a file. Click on the file to run the installer.
You can download the TunnelBear app in Google Play for Android devices and access the tool for macOS and iOS devices at the Apple App Store.
Click through the install wizard – each page has a funny, bear-related description of what’s going on: unboxing the bear, brushing fur.
When the installation completes, you need to set up an account. This requires you to enter your email address. If you want to stay completely anonymous, create a webmail account and use that for your TunnelBear setup.
Switch to your email Inbox and open the verification email. Click on the Verify my account in the email.
The app shows you a short guide on how to use the system. Click through this to get to the main screen of the VPN app.
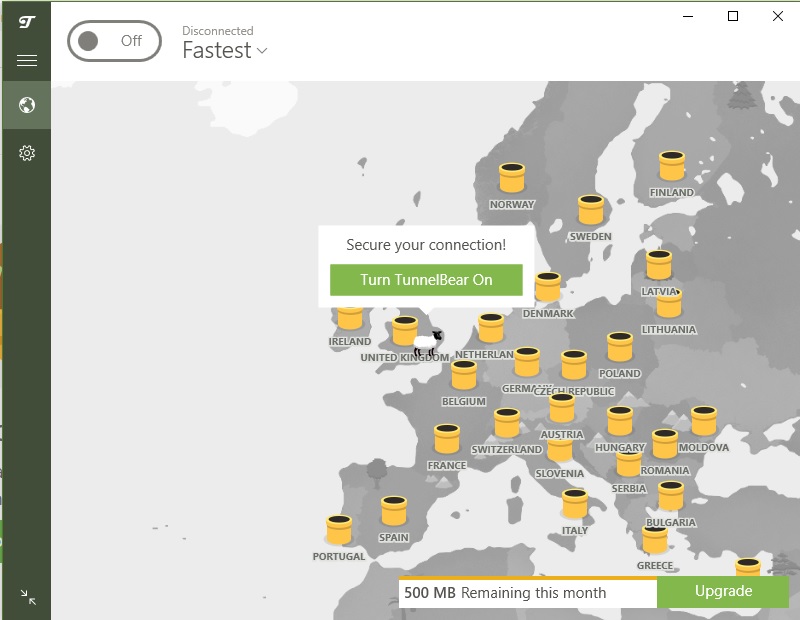
The main element on the app’s home page is a map. This shows a honey pot for each country in which the VPN has servers. Your location is represented by a sheep – this is the unprotected you.
Click on a honeypot to connect to a server in that country. The sheep turns into a bear, which digs a hole in the ground. A line to the chosen honeypot appears – this is the bear’s tunnel. When the VPN connection is established, the bear pops up in your chosen location.

If you turn the VPN off with the slider at the top of the Home screen, the tunnel goes back to the hole it dug and waits. You can reconnect to the last location by just clicking the slider to the On position.
There is no server list in the app – the map is the only way to select a location, and there isn’t an option to choose a location down to the city level.
To change the active VPN protocol, click on the cog symbol in the left-hand menu strip and click on the Connection tab. The VPN option is at the bottom of the screen.

The TunnelBear mobile app looks very similar to the desktop versions. However, there is one important difference – the Android and iOS apps offer a list of server locations as well as a map.

Speed tests
We examined the performance of the TunnelBear VPN service to see its influence on connection speed. These tests were performed in the UK on the Three networks. Tests were carried out using the Ookla system at speedtest.net, and the VPN protocol in the app was set to OpenVPN without the TCP Override. Each test scenario was run three times, and the middle result is shown.
To establish a performance baseline, we tested a connection to a nearby server without the VPN turned on:

The mean download speed achieved was 8.83 Mbps, and the upload speed was 2.08 Mbps. Turning on the TunnelBear VPN, set to use the server location in London, UK, and connecting to the same test server got these results:

This test gave a download speed of 9.10 Mbps and an upload speed of 1.84 Mbps. This shows an improvement in the download speed and a slight dip in the upload speed. However, this can be accounted for in the normal variability of the underlying service from the ISP.
Connections to faraway places across the internet are usually slower than connections to nearby servers. This is because it takes time to travel and also because the data packets get processed by more routers, each causing a tiny delay. This test went to Sydney, Australia:

As can be seen, a connection to the other side of the globe wasn’t much slower than a local connection. The connection had a download speed of 8.52 Mbps and an upload speed of 4.01 Mbps.
Turning on the TunnelBear service, using the London VPN server, and connecting to the same server in Sydney again, the results were similar to those using the VPN on a local connection.
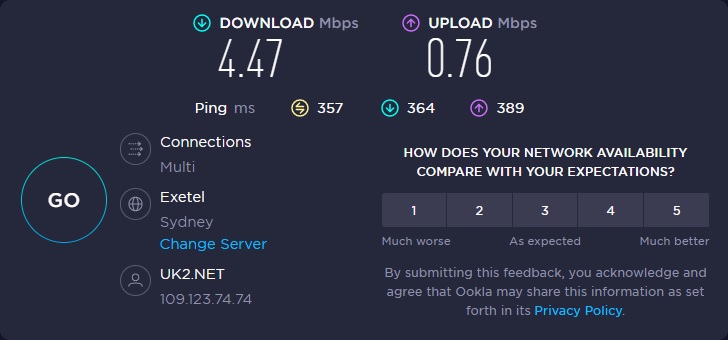
The download speed fell considerably to 4.47 Mbps, and the upload speed fell to 0.76 Mbps.
As cross-border access to video streaming systems is one of the main reasons that people subscribe to VPN services, the big drop in transmission speeds on long-distance connections with TunnelBear VPN is worrying. However, this drop in speed didn’t slow down the delivery of video streams from faraway countries.
FAQs
Does TunnelBear VPN work in China?
Using the GhostBear option in the TunnelBear app makes the VPN traffic look like regular HTTPS connections. The Chinese authorities would never block HTTPS because this is the system that makes eCommerce possible. Thus, TunnelBear is a very good choice for use in China.
Can I use TunnelBear VPN for torrenting?
TunnelBear has no problems with customers using the system to protect P2P file sharing.
Is TunnelBear a fast VPN?
TunnelBear slows down connections, although the loss of speed is great enough to be noticeable when streaming video.
Does TunnelBear include an ad blocker?
The TunnelBear VPN app doesn’t include an ad blocker. However, the company produces a separate browser extension called TunnelBear Blocker, which is a tracker and ad blocker. It also blocks pixel trackers in emails and ultrasonic tracking methods.
Does TunnelBear block infected files?
TunnelBear doesn’t inspect the contents of incoming packets, so it has no way to search for malware. You still need to run an antivirus system.
To sum it up
TunnelBear offers a great way to familiarize yourself with VPN technology. The system’s bear animation is great for encouraging kids to turn the service on. The fun bear-related terms that the TunnelBear system uses for VPN technology are endearing, and it keeps customers on board by creating an in-joke.
You only get an allowance of five simultaneous connections with a TunnelBear account, which is the same allowance that you would get with ExpressVPN and VyprVPN but less than the device allowance of NordVPN (6), CyberGhost (7), Proton VPN (10), and TorGuard Pro (12). Windscribe, Surfshark, IPVanish have no account limit on the number of devices that can be connected to the service simultaneously.
The ability of TunnelBear to get into Netflix and the BBC iPlayer beats a lot of the competition. However, it wasn’t able to get cross-border access to other systems, particularly Disney+. Before paying for TunnelBear VPN, test the service with the streaming system that you like to use by accessing the Free edition.





