Perimeter 81 Review (2024)
Perimeter 81 is a new platform of virtual network and security services. This provider is geared toward products for business, not private individuals. These products contain secure virtual networks for businesses that deploy both on-premises and cloud-based systems, and they are particularly useful for companies that operate a virtual office with dispersed, home-based team members who get remote access to the virtual corporate network from their own devices. Perimeter 81 advances from a standard business VPN to offer virtual network management. However, there are VPN services interlinked into the structure of the Perimeter 81 architecture.
What we like
- Presents a range of secure networking options
- Site-to-site connection protection
- Cloud security posture management
- No data metering
What we don't like
- 24/7 customer support only included in the top plan
- Doesn’t present specific solutions
- Requires you to pay for an account with a third-party identity management provider
Perimeter 81 background
Perimeter 81 is the second successful internet security company started by its founders, Amit Bareket and Sagi Gidali. The pair first created Safer Social Ltd, which produced the Safer VPN system. The consumer VPN provider soon extended its interests into business VPN services.
The pair split off the business VPN service into a separate band, Perimeter 81, in 2018 and then sold off Safer Social Ltd in 2019. Bareket and Gidali now run Perimeter 81 from headquarters in Tel Aviv, Israel, and development and sales offices in Los Angeles and New York.
The basic concept of all Perimeter 81 services is to provide a corporate network over internet connections. This can connect sites or individuals through a hub, which creates a software-defined network. Adding in third-party cloud firewall services, that corporate network gets a security front, making SASE, secure web gateways, and other network security configurations possible. So, the product family of Perimeter 81 grew.
Rather than offering a SASE, Zero Trust Network Access, and SD-WAN options, Perimeter 81 provides packages of tools, and the customer decides how to configure them to create an SD-WAN, a SASE, a Secure Web Gateway, and so on.
Think of Perimeter 81 as a toolkit for virtual networks. A subscriber doesn’t need to use all of the components in the package. In fact, planning the exact purpose of a Perimeter 81 subscription guides the network manager to accurately size requirements and choose one of the four Perimeter 81 cybersecurity plans.
Features
The underlying security mechanism of Perimeter 81 is a VPN network that runs through the Perimeter 81 server. These can be endpoint connections into the corporate network or site-to-site connections. Site-to-site can also connect to cloud platforms. Therefore, the Perimeter 81 server acts as a hub for all of the business’s internet traffic.
The company offers the following services:
- Secure Web Gateway (SWG)
- Software-defined WAN (SD-WAN)
- Software-defined Perimeter (SDP)
- Cloud Access Security Broker (CASB)
- Secure Access Service Edge (SASE)
- Zero Trust Network Access (ZTNA)
- Firewall as a Service (FWaaS)
The Perimeter 81 system operates in the market of secure edge services. Edge service is the type of system that you would expect to place on the boundary of a network. The types of functions you would get from an edge service are traffic management, data loss prevention, control over Web access, and security for internet connections, such as that provided by firewalls.
When you examine a typical edge service, you will wonder how it can be safe to move network protection out into the cloud. What about the link between the service and the network> Doesn’t that introduce a security weakness? You will discover that edge providers secure that link with a permanent VPN.
The founders of Perimeter 81 started out operating a VPN service, and when you look at the Perimeter 81 service, you can see that it is constructed with a VPN but has user and application management tools added on. Identity and access management systems in the management console create the difference between a VPN and an edge service.
The Perimeter 81 team claims that their service is not just a VPN but a higher-level of business service. They are right, and the ability to connect sites and cloud platforms together creates extra functionality that you don’t get with a VPN package.
Privacy and security
External endpoints get a client that enables them to log into the company network. This client is available for Windows, Linux, macOS, iOS, and Android. Site-to-site connections can be forged from Windows Server or Linux hosts.
User validation in the endpoint app can be tied into a single sign-on environment via a list of third-party services, including:
- Active Directory
- Azure AD
- Google Workspaces
- Okta
- Duo Security
Two-factor authentication is also possible through SMS or push notifications to mobile devices or through the Google Authenticator app.
VPNs operate according to rules set out in protocols, and there are a number of VPN protocols available. Perimeter 81 uses the WireGuard Protocol, which has the Advanced Encryption Standard (AES) as its encryption cipher. The AES implementation uses a 256-bit key, which is uncrackable.
WireGuard is a relatively new VPN protocol and is becoming widely expected because its efficient code has little impact on bandwidth and has low latency, enabling fast transfer speeds.
Secure Web Gateway (SWG)
The dashboard for the Perimeter 81 service is presented in the cloud, and it includes options for Web access controls. Although remote-based individuals get an interface to control whether the connection through to the Perimeter 81 is on or off on their account, they don’t get unfettered access to the Web while they are connected to the corporate network.
System managers can limit access to websites through the management console, making the Perimeter 81 account into a secure web gateway (SWG). This is achieved by providing a DNS server for all connected endpoints and then applying DNS filtering, which removes the IP address mappings for banned domains. This makes it impossible for the browsers on connected devices to access those sites while connected.
User-owned devices will revert to their own default DNS server when disconnected from the corporate network, enabling users to do what they like in their own time.
Traffic passing through the Perimeter 81 server between sites doesn’t need to be filtered with Web access rules.
Firewall as a Service (FWaaS)
While the secure Web gateway controls traffic traveling out of the virtual network, turning that functionality around provides a cloud-based firewall. As with the SWG, the firewall edge service only applies controls to traffic that interfaces with the outside world.
Perimeter 81 is part-owned by SonicWall, a California-based rival virtual network system, and there is some commonality between the SonicWall FWaaS and the firewall system offered by Perimeter 81.
The Perimeter 81 is implemented as a reverse proxy. If a business doesn’t run a Web server on its own premises, then all incoming traffic will only ever be in response to outgoing requests. This requires a typical VPN service where outgoing requests have the VPN server’s IP address in the header as the return address for the response. This is a useful security measure because it obscures the business’s real IP address.
There are many types of attacks that can be automatically blocked by keeping an IP address secret. For example, if anyone wanted to launch a Distributed Denial of Service (DDoS) attack against the company, they would have to direct that traffic flood at the only IP address that they know for the business, which is actually the IP address of the Perimeter 81 server.
As DDoS traffic has no content, it cannot be forwarded – there is nothing to send on. Thus, the Perimeter 81 server automatically absorbs all attack traffic.
Similarly, it is impossible for outsiders to identify the IP addresses of any of the endpoints on the corporate network. These devices could be user-owned computers and mobile devices that have been dedicated for business use while connected to the system through a Perimeter 81 VPN connection. Therefore, remote workers can safely communicate with customers and business partners without the risk that they will be targeted outside of the corporate system.
While all incoming traffic passes through the Perimeter 81 server, it can be scanned for malware and also for banned content. Thus, the Perimeter 81 system filters out harmful traffic before it reaches any of the equipment of the protected company and its users.
Software-defined WAN (SD-WAN)
One of the reasons that the Perimeter 81 system offers a package of tools rather than set virtual network solutions is that all of the newly emerging hybrid network systems are very similar. In some cases, the difference between different types of virtual networks boils down to different vendors using different names for the same concept. In other cases, just a small tweak in the services on a network can alter its definition from one category of the system to another.
The software-defined WAN is central to all of the other network configurations possible with the Perimeter 81 package. Basically, you just change a definition slightly or add on service and the SD-WAN becomes something else – as will be made clear when you read the following sections.
The true definition of an SD-WAN is that it operates as an overlay network and is mainly concerned with applying a unified private IP address pool across sites. Strictly speaking, Perimeter 81 doesn’t offer this because it only replaces the IP addresses used on the virtual network used by some devices. For your sites, the LAN IP addresses stay the same as those issues locally.
It is possible to model a unified addressing system without forking out for an extra IP address management tool with SD-WAN capabilities. You just assign non-overlapping address pools to the DHCP server on each of your sites. That way, you treat each site as a segment, with a router guarding it. Individual devices connecting through VPNs from remote locations get assigned substitute IP addresses. This is not a tidy solution, and you can’t control the address allocation. However, it does allow separate LANs to work together as a supernetwork.
When considering the SD-WAN concept as implemented by Perimeter 81, you are looking at the internal traffic of your business. Even those links that cross the internet between sites are considered to be internal, as are the branches out to remote devices.
BYOD policy is easy to implement with the Perimeter 81 system, as is the inclusion and tracking of roaming devices. Network access is granted to the user rather than to the device. Devices just need to have a Perimeter 81 client installed on them to enable them to connect to the network. This means that user-owned devices within your building are really treated as though they were elsewhere.
A user bringing a laptop into the office or wanting to connect with a mobile device connects to the Perimeter 81 service by logging in through the Perimeter 81 app. This transports traffic out to the cloud-based Perimeter 81 VPN server, which will then forward it back into the office, where it can access local network facilities. This seems like a big round trip for traffic to get from a BYOD laptop to a desktop computer sitting a few feet away. However, it simplifies security, and the low latency of the Perimeter 81 system means that the cost of speed for this simplified access model is negligible.
As far as remote access is concerned, it doesn’t matter whether the remote user is connecting from a desktop computer in the home or on a mobile device using a public wi-fi hotspot or the phone’s data plan. The device is not important, just the client software installed on it. Hence, the network is software driven and based on user access rather than hardware fixated.
Cloud Access Security Broker (CASB)
A Cloud Access Security Broker service controls access to a range of cloud systems. This is the cloud end of your single sign-on environment. CASB systems can interface with the access and permissions systems of platforms such as Google Workspaces and Microsoft 365 to control access by corporate users.
Perimeter 81 includes a centralized identity and access management (IAM) tool that is linked through to the user account for the access app on the user’s devices. Thus, the Perimeter 81 system flows through access rights from its own screen through to the cloud applications that you subscribe to for use by your team. Clearly, different departments will need access to different SaaS packages, and this distinction is taken care of in the definition of access rights within the Perimeter 81 management console.
Software-defined Perimeter (SDP)
The description for the CASB above can just be repeated to explain the Software-defined Perimeter service of Perimeter 81. The SDP concept revolves around a controller that validates users and grants access to different parts of the virtual network.
Imagine the Perimeter 81 app as a VPN client. The user logs in, picks a VPN server, and turns the VPN on to create a secure connection. Add in a single sign-on feature to that, and the secure connection takes care of logging into cloud services or network resources.
The system manager gets a console in the Perimeter 81 website that is like an Active Directory manager. You create user accounts and groups and then assign users to groups. You then also have a list of resources to which you link the groups. You can specify different permission levels for access to a resource.
By this method, you can let some remote users get into the network for one site but not another. You can let any user whether on a site or at home access a cloud service, such as Salesforce, Microsoft 365, and Azure system, an AWS service, or a tool on Google Cloud Platform. It doesn’t matter where those resources are located – they could be on-premises or in a cloud environment. Once the user has logged into the system through the Perimeter 81 app, the SSO service flows through user authentication.
Centralized controls of all access to resources make onboarding and offboarding very easy. If a user leaves the business with just a few clicks, that ex-employee loses access to all company accounts.
Secure Access Service Edge (SASE)
SD-WANs create unified supernetworks from a series of LANs. That definition caters to in-house infrastructure being connected by internet links. However, the typical modern business also subscribes to cloud resources. Connections to those cloud environments are not included in the SD-WAN remit. Rather, they are part of Secure Access Service Edge. Add cloud services into an SD-WAN system, and you get SASE.
SASE is a concept that was created to cater to hybrid environments, that is, businesses that use both on-premises systems and cloud services. So, you don’t need to have a multi-site operation to use a SASE. Just connecting your one site to one or more cloud services and centralizing access rights to them means you have created a SASE.
The “secure access” part of that name is taken care of by the VPN system that links each site to a cloud service and each remote user or mobile device to the company’s site and cloud accounts. “Edge” is a term that is applied to cloud-based network services, which usually provide security and/or traffic management. As Perimeter 81 is provided from its cloud-based server, all of the functions that it delivers are classified as edge services.
Zero Trust Network Access (ZTNA)
Zero Trust Network Access is another name for Software-defined Perimeter. While some providers might put a slight spin on the definition of ZTNA to make it sound a little different, it is, essentially, a cloud-based access rights manager that can cater to on-premises resources or cloud packages.
An important concept to stress here is that the single sign-on system that is built into the Perimeter 81 service isn’t a free-for-all. It doesn’t mean that anyone signing in and getting authorization to access the SD-WAN automatically has access to all of the tools and services that the company owns or subscribes to.
Access is controlled, so some users will get access to some resources while others won’t in fact, users who don’t have access to service won’t even know that it exists because they won’t see it on their desktops and they won’t be able to get to it through their browsers.
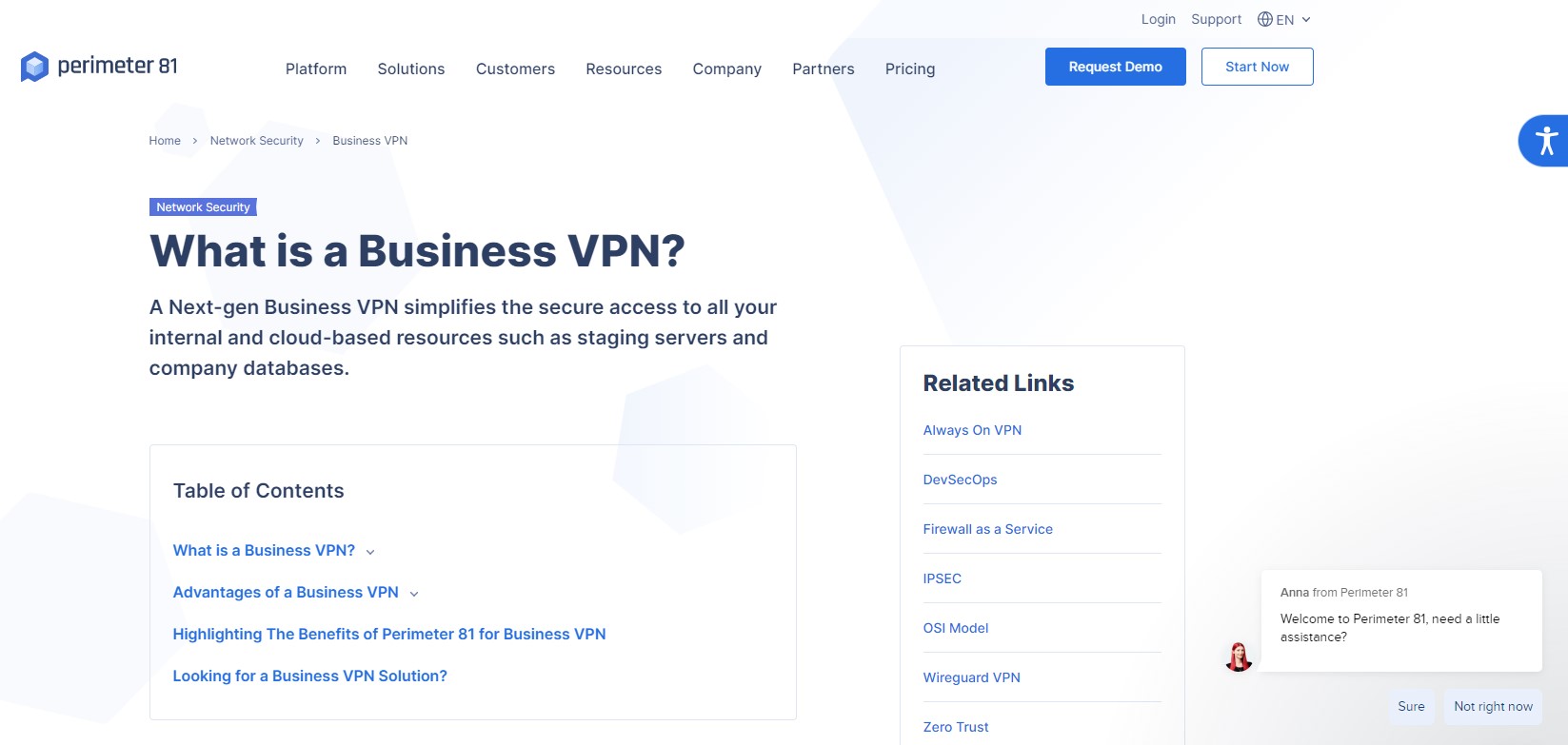
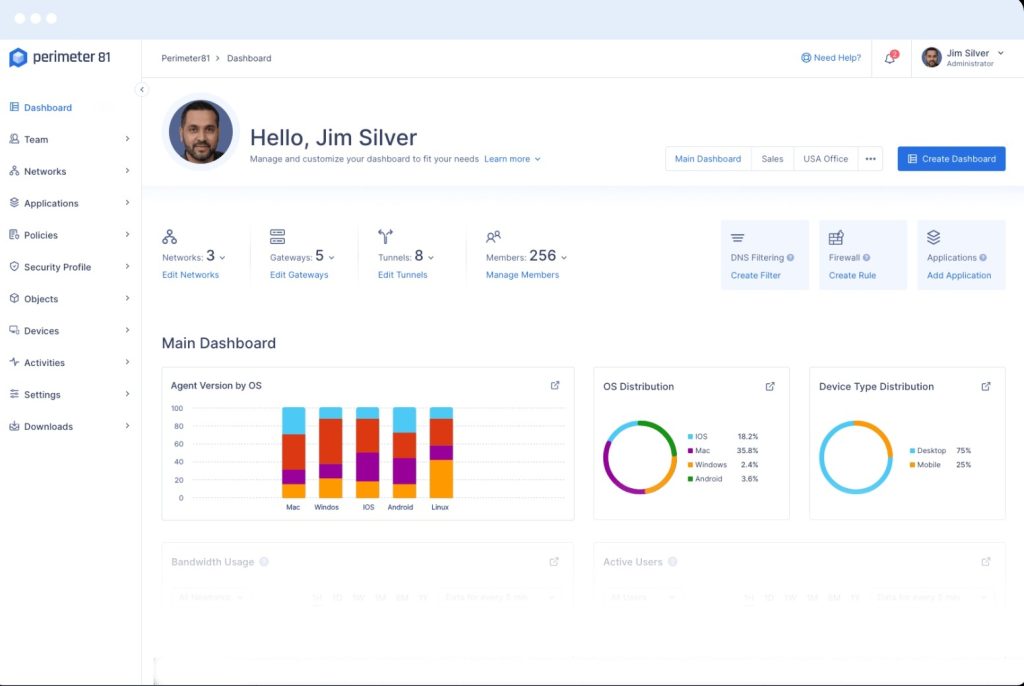
Perimeter 81 management dashboard
All subscriptions include a system administrator account that gets access to the hosted Perimeter 81 cloud network management platform. This is where you create a virtual network, which involves downloading an agent onto a server on each network, each cloud platform, and each remote user device. Perimeter 81 claims that a typical business can set up its virtual network in about 15 minutes.
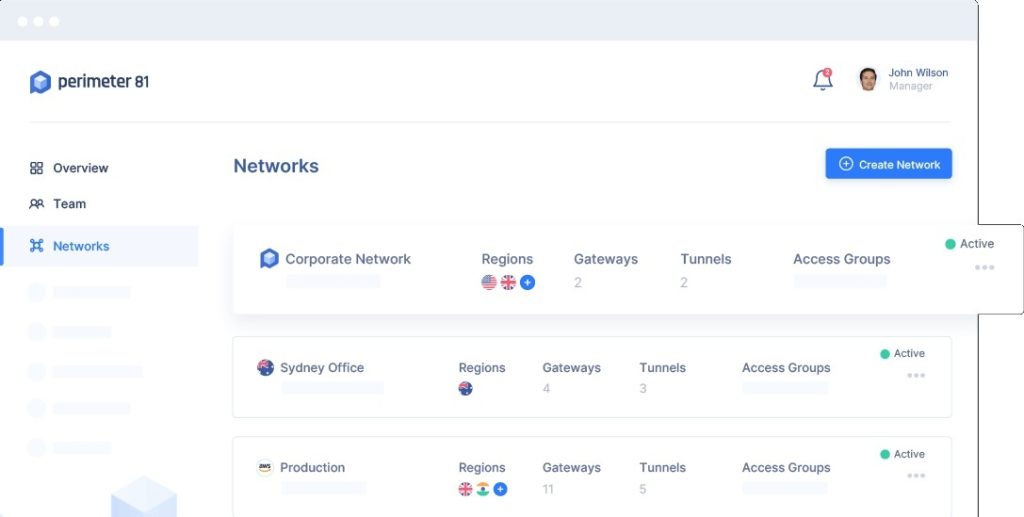
Another important tool on the dashboard is the identity and access management system, where you set up all of the user accounts, specify authentication methods and allocate accounts access for different cloud or on-premises services.
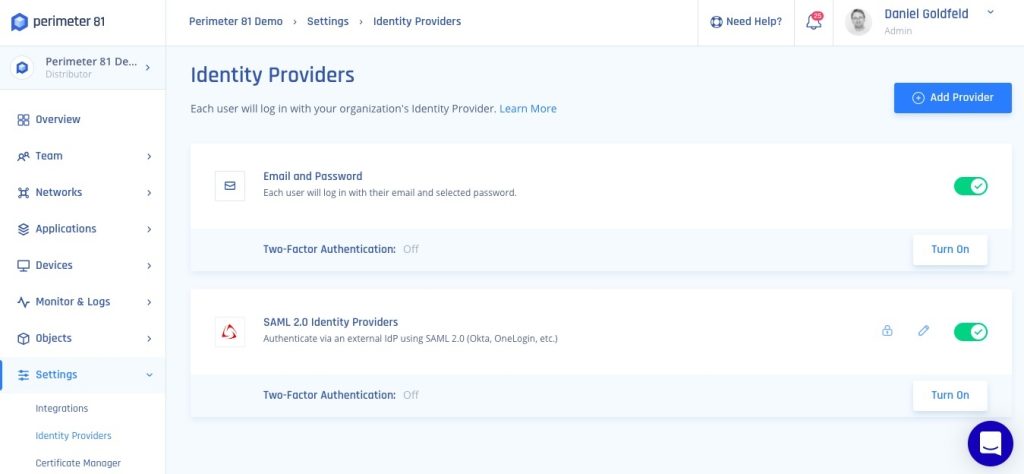
Identity Management in Perimeter 81 is heavily dependent on third-party identity and access management systems, and you need to set up and pay for an account with one of those separately from your Perimeter 81 account.
Perimeter 81 works with identity management solutions provided by:
- Azure AD
- ADFS
- Auth0
- Rippling
- Okta
- OneLogin
- PingIdentity
- PingFederate
- JumpCloud
The console also includes a monitoring dashboard, which provides constant network visibility and insights into user activity and application access. The statistics shown in the dashboard are updated every one to two minutes and processed into charts and graphs by the Perimeter 81 server.
Perimeter 81 User Agent
The employees of your company will connect to the network through a secure connection that is activated through the user agent. This is available for Windows, macOS, Linux, iOS, and Android.
Device posture check
Although the User agent can be installed on any device, the security of that device might alter over time. The device posture checks feature of Perimeter 81 scans each device’s security statuses before allowing a connection into the corporate network from it. This check can be specified by you and compiled in the management dashboard from a list of available factors.
The attributes that you can select for the device posture check include whether there is an active anti-virus system on the device and whether the operating system is up to date.
Pricing
Perimeter 81 offers four plans. These are called:
- Essentials
- Premium
- Premium Plus
- Enterprise
As you can probably imagine, Essentials is the cheapest plan, and Enterprise is the most expensive. The number of services included in each plan increases with progressively higher-priced packages. All plans include a 30-day money-back guarantee.
The Perimeter 81 service is not intended for use by private individuals – it is a business package. The plans are also not structured for very small consultancies, such as an own-operated one-person consultancy. Each plan has a minimum number of accounts that can be subscribed to because this is a team package.
One account is the system administrator account and lets a system manager control all of the services available within the created virtual network, granting access to user accounts.
Part of the price you pay for the service is calculated by the number of gateways that you access. This doesn’t refer to your network gateways but the Perimeter 81 data centers. There are more than 40 of these locations around the world, spread out across 25 countries. By connecting each user to the nearest data center, you get benefits in speed and security. If all of your users are in one location, you will only need to access one gateway.
The Secure Web Gateway feature is a paid add-on for all of the Perimeter 81 plans.
Essentials plan
The Essentials plan is available for a team of a minimum of five users. This plan is suitable for businesses that want to create an SD-WAN or a SASE for inter-site traffic and for secure access to cloud systems. The plan doesn’t provide a dedicated IP address for external access, so it isn’t suitable for networks that intend to serve outsiders. Traffic is allowed into the network, but only in response to a request that originated within the network.
The service costs $8 per user per month plus $40 per month per gateway when paid annually. That means the charge would be $96 per user and $480 per gateway because you have to pay for the entire subscription period upfront.
If you choose to pay monthly, the price is $10 per user per month plus $50 per gateway per month.
This plan provides the following services:
- Global private network
- Web-based, secure application access for two applications
- Zero Trust policy-based segmentation, which provides permission levels for each protected application
- Unlimited data usage
- Activity audits & reports with data retention for 14 days
- Cloud gateway speed of 500 Mbps per gateway
- Unlimited network tunnels that fix secure links between sites and cloud resources
- Site-to-Site interconnectivity that also extends to cloud platforms
- Split tunneling for options over whether to leave traffic to some destinations unencrypted
- Private DNS that allows you to use your own DNS server
- Two-factor authentication with SMS or two-factor authentication
- Easy-to-use apps to allow remote workers to connect to the network
- Wireguard protocol for connection encryption
- Automatic Wi-Fi security for mobile devices
- Self-service knowledge base for system managers to learn how to use the system
- Dedicated chat and email support during office hours
Premium plan
The Premium plan is the lowest of the plans for those businesses that need to allow incoming traffic. You will get a dedicated IP address for this purpose that fixes the address the Perimeter 81 system uses to represent your business in DNS servers around the world. This will give you an identifiable location through geo-location lookup systems, and you can choose which of the 40 Perimeter 81 data centers should host the address.
The Premium plan is priced at $12 per user plus $40 per data center per month when paid annually, which works out at $144 per user per year and $480 per gateway per year. The monthly payment plan is priced at $15 per user per month plus $50 per gateway per month. The Premium plan requires a minimum of ten users.
With this plan, you get:
- Global private network that connects all of your sites, remote users, and cloud services
- Premium public network to allow incoming connection requests
- Web-based, secure application access for 10 applications
- Zero Trust policy-based segmentation, which provides permission levels for each protected application
- Unlimited data usage
- Activity audits & reports with data retention for 30 days
- Firewall as a Service with 10 network access policies
- Cloud gateway speed of 1000 Mbps per gateway
- Unlimited network tunnels that fix secure links between sites and cloud resources
- Site-to-Site interconnectivity that also extends to cloud platforms
- Always-on VPN for secure access to third-party networks
- Split tunneling for options over whether to leave traffic to some destinations unencrypted
- Private DNS that allows you to use your own DNS server
- DNS filtering to manage user access to external websites
- Device Posture Check with three different device profiles possible
- Two-factor authentication with SMS or two-factor authentication
- Single Sign-On capabilities through a list of third-party systems
- Easy-to-use apps to allow remote workers to connect to the network
- Wireguard protocol for connection encryption
- Automatic Wi-Fi security for mobile devices
- User configuration profiles with up to three profiles
- Self-service knowledge base for system managers to learn how to use the system
- Dedicated chat and email support during office hours with a prioritized response
Premium Plus plan
The Premium Plus service has the same facilities as the Premium plan but with more capacity. This plan is available for $192 per user per year ($16 per month) plus $480 per gateway per year ($40 per month). On the monthly plan, the prices are $20 per user and $50 per gateway. You need to take out a minimum of 20 user accounts to get this plan.
You can set up this plan to feed activity data to your SIEM package for an additional fee.
This plan includes:
- Global private network that connects all of your sites, remote users, and cloud services
- Premium public network to allow incoming connection requests
- Web-based, secure application access for 100 applications
- Zero Trust policy-based segmentation, which provides permission levels for each protected application
- Unlimited data usage
- Activity audits & reports with data retention for 30 days
- Firewall as a Service with 100 network access policies
- Cloud gateway speed of 1000 Mbps per gateway
- Unlimited network tunnels that fix secure links between sites and cloud resources
- Site-to-Site interconnectivity that also extends to cloud platforms
- Always-on VPN for secure access to third-party networks
- Split tunneling for options over whether to leave traffic to some destinations unencrypted
- Private DNS that allows you to use your own DNS server
- DNS filtering to manage user access to external websites
- Device Posture Check with 20 different device profiles possible
- Two-factor authentication with SMS or two-factor authentication
- Single Sign-On capabilities through a list of third-party systems
- Easy-to-use apps to allow remote workers to connect to the network
- Wireguard protocol for connection encryption
- Automatic Wi-Fi security for mobile devices
- User configuration profiles with up to 10 profiles
- API support so you can integrate the system with your own frontend solution
- Self-service knowledge base for system managers to learn how to use the system
- Dedicated chat and email support during office hours with a prioritized response
- Dedicated customer success manager to assist you in configuring your services
Enterprise plan
The Enterprise plan is priced by negotiations, and some of the capacities allocated to this service can be upgraded. This plan is only available to businesses that sign up for at least 50 user accounts. SIEM integration is included in the price of this plan
The services in the Enterprise plan are the same as that for the Premium Plus plan but with extra capacity on some of the services. These are:
- Unlimited Web-based, secure application access
- Unlimited Firewall as a Service access policies
- Activity audits & reports with data retention for 60 days
- Unlimited Device Posture Check profiles
- Unlimited user configuration profiles
- 24/7 dedicated chat and email support
- 24/7 phone support
FAQs
What does Perimeter 81 do?
Perimeter 81 is an edge service that offers a system to provide a private corporate network over the internet. This can be implemented as a software-defined WAN (SD-WAN), a software-defined perimeter (SDP), zero-trust network access (ZTNA), or secure access service edge (SASE). It is also possible to manage external traffic, channeling through Perimeter 81 servers as a frontend that provides DDoS protection and FWaaS.
Is Perimeter 81 a VPN?
Perimeter 81 advertises its service as a step up from a VPN service because it provides a hub between users and sites. Effectively, remote users connect through to the system in an identical fashion as individuals using a VPN. Users on a LAN do not need the VPN app, however, because they are all included in the secure network through a virtual appliance that operates for the entire office LAN.
Does Perimeter 81 monitoring use a SIEM?
Perimeter 81 provides a monitoring service for networks, users, and applications, and the metrics that are gathered are retained on the cloud server for historical analysis. These statistics can be composed into log files for transfer into third-party systems with some of the Perimeter 81 plans. However, Perimeter 81 does not include its own SIEM service.
Where is Perimeter 81 based?
The headquarters for Perimeter 81 are in Tel Aviv, Israel. The company also has offices in Los Angeles and New York in the USA. There are Perimeter 81 data centers in 25 countries.
Do all users in a Perimeter 81 network need a VPN app?
Perimeter 81 provides a user agent utility, which is like a VPN app. This is available for Windows, Linux, macOS, Android, and iOS. The user agent is only necessary for devices that aren’t connected to the company’s LAN, such as remote users, roaming workers, or BYO devices. Office workstations are connected to the secure virtual network through the LAN’s gateway.
Final thoughts
Perimeter 81 is an innovative provider of edge services. This is a cutting-edge field, and so the services offered by the provider are still evolving.
Rivals in this new market sector provide specific secure network architectures, such as secure access service edge (SASE) or zero trust network access (ZTNA). Many of these edge service configurations are almost identical, and businesses might not fully understand what these off-the-shelf systems really mean.
With the Perimeter 81 service, the network manager defines the configuration of the virtual network system by picking the services that are required. Whether that combination of features results in an SD-WAN, a SASE, or a ZTNA configuration really doesn’t matter. What matters is that the company gets its internet links between sites, to cloud platforms, and from remote workers, managed and secured.
Many edge services complicate the presentation of their systems in order to enhance their perceived value and hike up the price. The Perimeter 81 team came from a VPN background, and so if you understand how VPNs work and how such a system can provide internet security for your business’s networked services, you can start to build up better services.
Connect all of your sites through the same data services with constantly connected VPNs, and you have an internet-based virtual network, add on a cloud-based firewall, control user access to cloud and on-premises applications, and before you know it, you have created a complicated and sophisticated virtual system that probably fits one of those industry buzzwords that you sometimes hear.