IPVanish Review (2024)
IPVanish is a veteran of the virtual private network market. The company made its name by getting Tier 1 access to Internet infrastructure and running its own servers for optimum connection speed. The only problem with this VPN provider is its base in the USA, which could make it vulnerable to pressure from copyright lawyers. In this IPVanish VPN review, we will examine whether it is worth subscribing to this VPN service.
What we like
- Good at dodging blackouts on US sports streaming sites
- A large IP address pool
- Split tunneling available
- Strong IP leak protection
- IPVanish support is available around the clock via chat and email
What we don't like
- No app for Linux
- No browser extensions
- 30-day money-back guarantee only for the annual plan
- Prices increase after the first subscription period
- No malware or antivirus service
Features
| IPVanish Features | |
|---|---|
| Rating: | 4.4/5 |
| Price: | $3.99 – $10.99 per month |
| Refund period: | 30 days |
| Based in which country: | USA |
| # devices per license: | Unlimited |
| # servers: | 2,000 |
| Server locations: | 75 locations in 50 countries, including USA, UK, Canada, Australia, India (virtual), and Hong Kong |
| Streaming sites unblocked: | Netflix, BBC iPlayer, Amazon Prime Video |
| Supports torrenting: | Yes |
| Does VPN keep logs: | No |
| 24/7 customer support: | Yes |
| Website: | https://www.ipvanish.com |
IPVanish was founded in 2012 by Mudhook Media, Inc. In Orlando, Florida. The VPN system is now a division of Ziff Davis, Inc., which also owns Strong VPN, Spiceworks, and Speedtest.net by Ookla.
The IPVanish team based their VPN service’s unique selling point on technical excellence. They created a Tier 1 backbone that connects directly to the Internet without using third-party carrier agreements. Until recently, the business’s servers were all owned and operated in-house.
The company’s server list is now 90 percent owned because the business found that some server locations, such as Albania, could be better provided by partnering with external data centers. Nonetheless, this is still one of the best VPN services for reliability and security.
Apart from its infrastructure, the most notable feature of the IPVanish VPN service is that it doesn’t limit the number of devices that can be connected to the service simultaneously. This is unusual because most VPN providers limit the number of simultaneous connections allowed per account to five, six, or seven. There is still one restriction, though, which is that the IPVanish VPN account can only be shared within one household. So, set up the VPN on your children’s mobile devices, but don’t give out your login information to friends.
IPVanish works in much the same way as many of its rival VPN providers, with a choice of VPN protocols and encryption for internet connections. VPN users look for a way to get around account location restrictions at Netflix, and the ability to get past the proxy detection system of that service is the hallmark of the top VPNs. IPVanish has that ability plus the power to dodge geolocation restrictions at a long list of streaming services.
Privacy and security
The IPVanish system offers strong privacy protection and several features in the IPVanish app to add on more security options. The security of the IPVanish service isn’t quite as strong as some of its leading rivals, such as ExpressVPN and CyberGhost.
IPVanish location
IPVanish’s location in the USA is probably its biggest security weakness because despite keeping no logs, it is vulnerable to legal action and pressure from official government bodies, such as the NSA. The company swears that it does not cooperate with authorities in respect to logs and has even had its system audited by a third-party verifier to prove that.
There is one known instance when the VPN provider handed over activity records on one of its customers to the Department of Homeland Security. Admittedly, this was in 2016, which is a very long time ago and doesn’t exactly reflect on the practices of the VPN service today. However, it does mean that the company doesn’t have a clean sheet when it comes to privacy protection.
The information provided to the Department of Homeland Security included the customer’s email address, IP address, and timestamps of when the person was connected to the service. At the time, as today, IPVanish stated on its website that it didn’t collect such information.
The event raises suspicions over the veracity of the IPVanish no-logs policy. Attempts by customers to create anonymity are confounded by the payment collection system for the IPVanish service, which doesn’t offer anonymous payment methods such as gift cards or tokens. IPVanish used to accept Bitcoin for payment, but now subscribers need to pay by credit card or PayPal, which makes them traceable.
How IPVanish VPN works
A virtual private network (VPN) offers connection privacy over the internet in two phases. All traffic from the subscriber’s device is sent through a VPN server, no matter where its ultimate destination is. The VPN service acts as a front end for that user and receives back responses to outgoing requests.
A VPN session is traditionally called a tunnel. This is because the traffic can’t be seen or examined for information about its correspondents. They will just see the address of the VPN server. This is because each packet is fully encrypted and then placed inside a carrier packet – a process that is called encapsulation. The outer packet is addressed to the VPN server.
The VPN server receives each packet, removes its protecting encryption, and then sends it to its intended destination, but it puts its own address in the packet as the source IP address. Thus, when the remote server checks the origin of the request, it sees the VPN server’s address. Lookup systems that reference IP addresses to physical locations come up with the location of the VPN server. This is why VPNs offer a range of locations.
A website that only allows access to visitors from specific locations can be tricked by this source address substitution. As the web server only knows the VPN server’s IP address, it has no idea that it is really dealing with someone that it would otherwise block on location grounds. It replies to the VPN server, which readdresses the reply and sends it back to the customer.
There are different methods that a VPN system can use for this address manipulation. Some use one IP address for all outgoing traffic and identify each individual customer with a port number. IPVanish allocates a temporary IP address to each customer. The company has over 40,000 IP addresses, with a pool of some of those held by each server. When a customer connects to a VPN server, one of those addresses is allocated. At the end of the session, the address is returned to the pool for use by another customer.
IPVanish VPN protocols
IPVanish subscribers get a choice of VPN protocols. The VPN protocol in operation can be specified within the IPVanish app. A protocol is a set of rules and guidelines that are widely used for many aspects of networking and internet functionality. This is because both sides in a connection need to follow the same coding standards and neutral protocols allow systems created by different companies to have compatibility.
The VPN protocols that IPVanish offers are:
- WireGuard for Windows, macOS, iOS, Android, and Amazon Fire OS
- IKEv2 for Windows, Linux, macOS, iOS, and Android
- OpenVPN for Windows, Linux, macOS, Android, Chrome OS, Amazon Fire OS, and routers
- L2TP with IPSec for Linux, macOS, iOS, and Android
- SSTP for Windows
PPTP is not supported by IPVanish.
- WireGuard is a new VPN protocol, and it is the default system used by IPVanish. The protocol is known for being fast at processing data and so is appropriate for IPVanish, which prioritizes speed as its unique selling point.
- OpenVPN is the most widely used VPN protocol, and most of IPVanish’s rivals offer this as the default protocol. It is an open-source protocol. The system is very thorough and secure, but it does require a lot of processing. Data transmissions are governed by networking protocols, and one of these, the Transmission Control Protocol (TCP), ensures that all packets arrive and are in sequence. This system is offered with the OpenVPN option, but you can turn that off and go with the faster User Datagram Protocol (UDP) instead for greater speed.
- IKEv2 is usually paired with IPSec, but the IPVanish website doesn’t mention the IPSec association. This is a lighter protocol than WireGuard and OpenVPN and so is preferred for mobile devices because it puts less strain on the smartphone’s battery.
- IPSec is listed separately from IKEv2 by IPVanish, and it isn’t used with the same list of operating systems. However, it is rare that IPSec is used by itself. Key management is often provided by IKEv2 or L2TP for IPSec. As IKEv2 is listed separately, it can only be assumed that the IPVanish IPSec implementation partners with L2TP.
- SSTP is a Microsoft system that creates a tunnel using the SSL system, which is now provided by Transport Layer Security. The service switches to stronger encryption for actual data transfers. This option is only available in the Windows IPVanish app.
IPVanish encryption
The connection between the VPN app, which is called the “client,” and the selected VPN server is encrypted. This blocks snoopers from getting into the information being transferred, including the IP address or the remote correspondent.
Data packets are encrypted by the Advanced Encryption Standard, which is better known as AES. This cipher was commissioned by the US government for use by its own agencies. The list of government organizations that use AES to protect internet transmissions includes the CIA and the US military. AES can also be used to protect data at rest on servers.
Although AES is considered very strong, the length of the key used is very important in strengthening or weakening the protection. The AES system has been published, so anyone can see how the cipher works. Potentially, that means it can be cracked. At the heart of the cipher is a formula that starts the transformation of the characters in an original piece of text. This includes a variable and changing the number that gets plugged into that completely changes the outcome of applying the cipher.
That variable in the AES formula is called the key. Anyone who wants to crack the encryption would just need to try out different values for the key until it found a number that made the scrambled text into something legible. This encryption cracking technique is very common, and it is known as a “brute force attack.”
AES blocks brute force attacks by providing very long keys with so many possible permutations that it would take thousands of years to guess. The longest key available for AES is 256-bits long, which is what IPVanish uses. You will see it written as AES-256.
IPVanish session establishment
AES is a symmetric key system, meaning you need the same key to decrypt a text as that used to encrypt it. This presents a problem because that means one side needs to generate the key and then send it to the other side.
Until the encryption key has been settled, there is no encryption on the connection’s end, so the encryption key would have to be sent in plain text. That presents an opportunity for snoopers to unlock all subsequent messages in the stream by capturing the key.
To cover the transmission of the AES encryption key, IPVanish uses procedures laid down in the Transport Layers Security protocol (TLS). This is the security system behind HTTPS, which makes all Web pages secure.
Under TLS, the connection establishment routines are protected by a public key encryption system. This is a cipher called RSA. A public key encryption system uses different keys to encrypt and decrypt data. You can’t guess the corresponding decryption key if you have the encryption key. Thus, it is safe to publish the encryption key, making it public, while keeping the decryption key private.
The RSA cipher can also be used for server authentication. This process blocks “man in the middle” attacks, where a snooper pretends to be the server. Under TLS, the RSA public key is held on a certificate (called an SSL certificate) by a certificate authority. Before connecting, the client gets the server’s SSL certificate and takes the RSA key. It then encrypts a challenge message and sends it to the server. Anyone intercepting the message will not be able to decrypt the challenge and answer it – only the genuine server has the associated decryption key.
IPVanish uses Diffie-Hellman exchange, which requires the client to have an SSL certificate as well. When the server communicates with the client, it encrypts the message with the client’s public key. Thus, both sides prove their identity.
Again, the strength of the cipher lies in its length. Public key systems have lower effective security than symmetric key systems, so they need to have much longer keys. IPVanish uses a 2048-bit RSA key. This is smaller than the RSA key length used by other leading VPNs, such as ExpressVPN and NordVPN, which both use an RSA key length of 4096 bits. However, IPVanish is not alone in its use of the 2048-bit RSA key – Surfshark and Private Internet Access also use it.
IPVanish DNS protection
You will have seen mention of IP addresses in this review. An IP address is an addressing system used on the internet. A central authority distributes blocks of IP addresses to national divisions to be made available to internet-enabled devices. Every IP address on the internet has to be unique, and its distribution method means it is very easy to work out in which country the device of the address is active.
You have probably never seen an IP address, and this is because your Web browser doesn’t need them. Instead, when you want to see a Web Page, you type its Web address (URL) into the browser address bar or click on a link, which puts that address there for you. Everything up to and including the “.com” (which is called a “top-level domain”) is the address of the website. Anything after the .com is the directory and filename for the HTML file that provides the Web page.
So, you’ve come to bestvpn.org. However, routers on the internet have no idea what that is. They are only interested in IP addresses. So, before sending a request for a file from bestvpn.org, your Web browser needs to get the address of the Web server for the site.
A system of DNS resolvers is used to speed up access to relevant sections of the cross-reference table. This is a service that is usually provided by your ISP, but big companies will have their own., The DNS resolver stores the most frequently requested website IP addresses and look there first. If the site address isn’t found, it fetches the address from a remote DNS server.
If a hacker can intercept your internet traffic, it is easy to direct your Web browser to a fake Web page that can harvest your login credentials for a service and even your bank account details. This is a process called DNS spoofing, and it involves maintaining a DNS resolver record for a given URL but pointing to the wrong IP address.
Internet service providers use this hacker trick to block access to many sites. Even if a site is legal, it is possible that your ISP won’t let you access it. You can take steps to shield information about your Web activities from your ISP’s government-mandated logging system by protecting your traffic with a VPN. However, if DNS queries aren’t protected, all of your website access is revealed – this is called a DNS leak.
IPVanish runs its own DNS resolver, and it doesn’t use it to block access to any sites. Once your VPN app is connected to a server, all of the DNS queries performed by your Web browser go to the IPVanish DNS server within the encrypted session created by RSA.
IP leak protection
The point of a VPN is to include a device into a remote network, protect all traffic between the device and that remote network, and control that device’s access to the internet through the gateway of that remote network.
The protection of traffic between the device and the network should be as private as though the device was actually located within the offices covered by that network. Therefore, no outsider should be able to see what internet addresses are on the traffic within that privacy tunnel between the device and the network.
If outsiders can see the contents of the packets that travel between the device and the network, there has been a security breach. That protection extends to the contents of header packets. If a packet header is revealed, that event is called an IP leak. It allows the online activities of the VPN user to be logged and manipulated.
A VPN service that does not protect the packets traveling in a VPN tunnel is not worth subscribing to, so it is very important that a potential customer can verify that the VPN actually works. Leak tests prove that as long as the IPVanish VPN is turned on, you will not get any DNS leaks, IP leaks, or WebRTC leaks. Your ISP will only be able to log that traffic passes back and forth between your protected device and your chosen VPN server.
IP leak issues arise if the VPN gets turned off without you realizing it. This situation does happen frequently because a break in the internet connection serving your device will end the VPN session, and you will have to start it up again. You might not notice that your internet connection dropped because there is a short period when your device will try to re-establish the connection. Usually, this works, and so normal activity resumes. To you, it would just seem that a Web page takes longer than normal to load.
To prevent the scenario of a lost internet connection resuming without the VPN, IPVanish has created a feature in its app called the Kill Switch. This blocks your network card so only traffic that has been processed by the VPN can be transferred onto the internet. So, if the VP is not active, there will be no internet available on your computer. This feature ensures that you notice when the VPN is turned off.
Other IPVanish app features
The IPVanish app provides two other important services.
- One is automatic Wi-Fi protection. Hackers can set up fake Wi-Fi hotspots in public places, control the encryption keys used over the wireless network, and then read all of the traffic of all of the people that mistakenly connected to that hotspot. With IPVanish, your communications are encrypted end-to-end, so even if the hacker unwraps the wireless system encryption, there will still be a layer of protection in place.
- The app also facilitates split tunneling. This system allows you to exclude certain traffic from the VPN’s protection. Keep in mind that your ISP will be able to log all of the connections you make outside the VPN tunnel. This is not officially termed an IP leak because it is intentional.
IPVanish SOCKS5 proxy
In addition to its VPN service, IPVanish offers an alternative route to changing your IP address. This provides online anonymity, and you can set the system up to provide you with an identity that appears to be located in another country. This is great if you are abroad and want to stop websites from detecting where you are and giving you the local version of the site instead of the version for your home country. News websites, Employment sites, and even search engines give you a different version according to where you are, and it can be very annoying.
So, if you just want to change your IP address and appear to e somewhere else but don’t care about your ISP logging your activities, using the SOCKS5 proxy might be more interesting. This is because your connection will be faster without the encryption processes running.
One problem with the IPVanish SOCKS5 proxy service is that it doesn’t come with an app. So, you either have to find a different interface for the service or set it up deep in the bowels of your computer’s network settings, which can be complicated.
Website blocking
The two main features of the IPVanish app are an on/off button and a location selector. Depending on whether you are on the desktop, set-top, or mobile app version, the location selector will be a map or a list. The server location is important because this choice enables you to circumvent the manipulations and blocks that many Web systems perform according to the visitor’s location.
You might want to get into a site that your government doesn’t want you to access, such as a gambling website when you are in India, or you might want to get into the version of a site for a country other than the one you were in, for example, the shows and movies that you can watch on Netflix is different when you are in the USA than it is in France.
There are many examples of how getting cross-border access to sites is so good that the owners of those Web systems don’t want you to do it. This is a particularly big issue with streaming services; those systems know about VPNs, so they try to identify VPN traffic and block it. In the VPN industry, getting cross-border access to Netflix is the touchstone, particularly access to US Netflix. Very few VPNs can do this, and IPVanish is one that can.
Here is a list of the streaming services that we tested with IPVanish
| Service | Test |
|---|---|
| Netflix | Tests confirmed access to USA, Australia, Japan, and UK libraries but not France |
| Disney+ | Worked for the USA but not for the UK or France |
| BBC iPlayer | Tests confirmed, accessing the UK from the USA |
| ITV Hub | Tests confirmed, accessing the UK from the USA |
| Channel 4 | Tests confirmed, accessing the UK from the USA |
| ABC | Didn’t work |
| NBC | Tests confirmed, accessing from the UK |
Other major streaming services that IPVanish gets cross-border access to include HBO Max. While it can unblock ESPN+, Amazon Prime Video, and Hulu, performance can be spotty with IPVanish – sometimes it works, and sometimes it doesn’t. IPVanish is very good for use with Kodi.
One important note to make is that when we say this VPN can get you into Netflix, Amazon Prime, or other subscription services, you still need an account with those streaming sites. What we mean is that the VPN can get into the service for another country, not that it can get you in without paying.
Pricing
IPVanish offers one plan that is packaged in three subscription periods. These are:
- Monthly plan: $10.99 per month
- Quarterly plan: $15.96 for the first 3 months ($5.32 per month)
- One-year plan: $47.89 for the first year ($3.99 per month)
Like most VPN providers, IPVanish doesn’t offer a free trial but gives new customers a money-back guarantee instead. The 30-day money-back guarantee offered by IPVanish is very similar to the guarantees offered by other VPN systems. However, with IPVanish, the guarantee only applies to the annual plan – the monthly and quarterly plans don’t get it.
Another issue to be aware of when comparing the prices of different VPN services is that those headline prices you see on the home page of the IPVanish site only apply to the first subscription period. After that, you are charged a higher price, and the subscription automatically rolls on and charges you again at the end of the subscription period. The real, long-term prices for the three plans are:
- Monthly plan: $10.99 per month (no change)
- Quarterly plan: $29.99 every 3 months ($9.99 per month)
- One-year plan: $89.99 every year ($7.50 per month)
Speed tests
We tested the performance of IPVanish in the UK on public Wi-Fi hotspots provided by Sky UK’s The Cloud. This service is owned by Comcast, which operates the same technology in the USA as the Xfinity Hub network. Tests were carried out using the Ookla system at speedtest.net.
These tests were performed with the desktop IPVanish app for Windows with the VPN protocol set to WireGuard, which IPVanish advises is its fastest option.
First, we tested a connection to a nearby server without the VPN turned on:
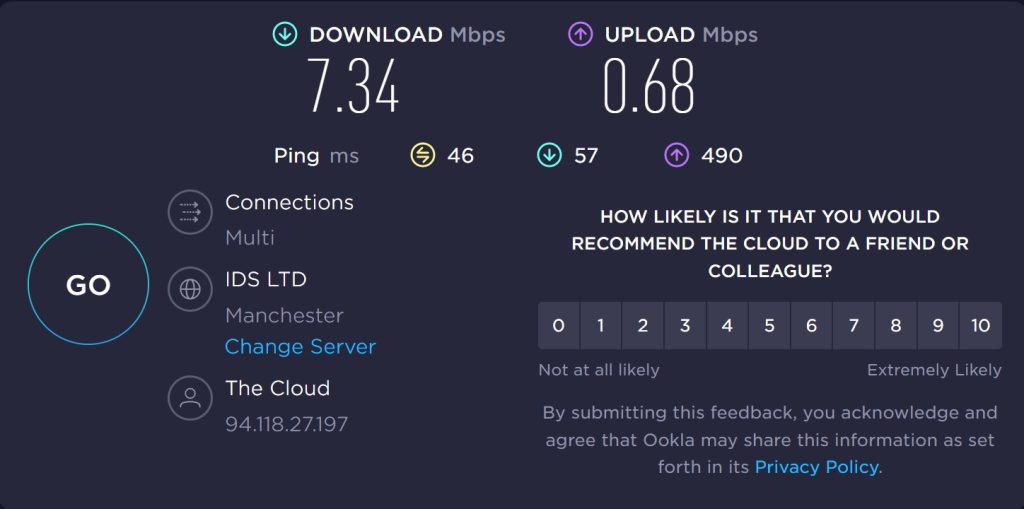
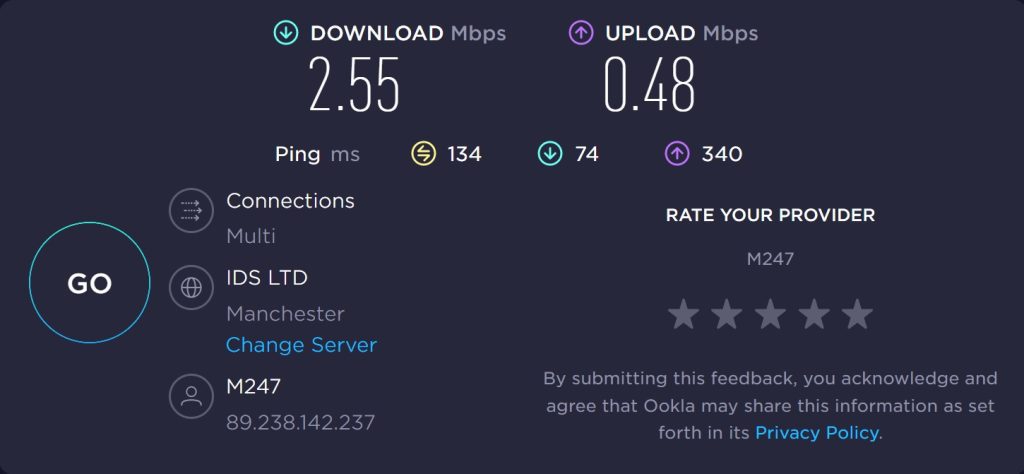
The download speed shown was 7.34 Mbps, and the Upload speed was 0.68 Mbps. As can be seen below, turning on the VPN, set within the UK, in the same city as the Speedtest server, made a big difference to performance, lowering download speed to 2.55 Mbps and upload speed to 0.48 Mbps.
Long-distance connections with this ISP do not do very well – this test went to Sydney, Australia:
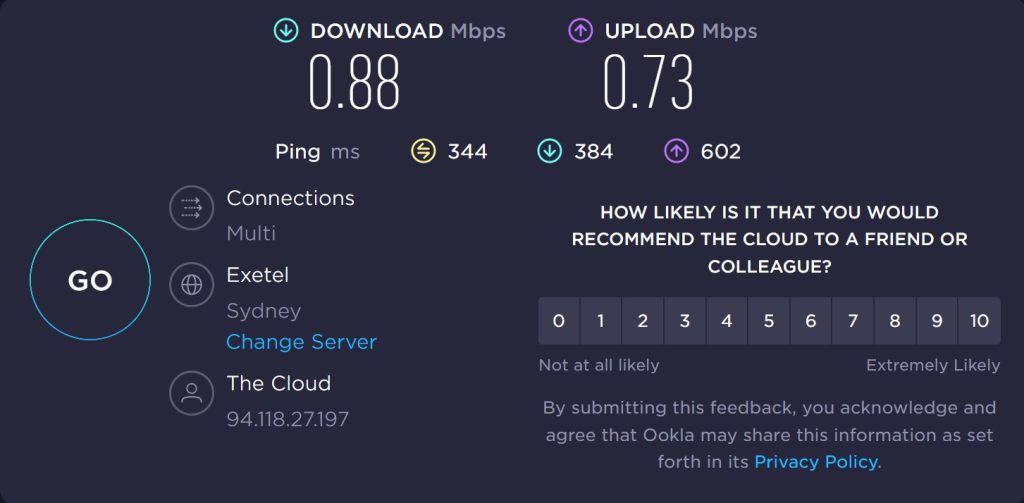
This shows that routing across the world does slow down the delivery of websites and video streams. The download speed fell to 0.88 Mbps, but the upload speed increased to 0.73.
Channeling through the IPVanish Manchester made little difference to latency:
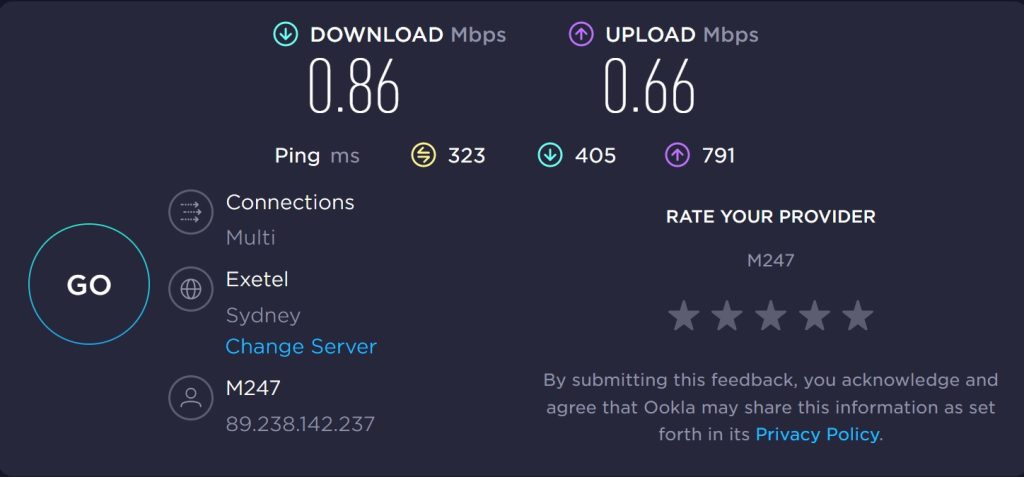
The download speed was 0.86 Mbps, and the upload speed was 0.66 Mbps.
Connecting to Sydney through a VPN server in New York, USA, gave a download speed of 1.55 Mbps and an upload speed of 0.84 Mbps. Connecting to Sydney while channeling traffic through the IPVanish server in Tokyo, Japan, gave a download speed of 1.52 Mbps and an upload speed of 0.56 Mbps.
Although the extra work that a VPN performs can be expected to slow down internet connections, on local connections, IPVanish slowed download speeds to half the unprotected speed. On identical tests, NordVPN and ExpressVPN significantly increased connection speeds on international links.
How to install
- Select a plan from the IPVanish Home page. In the Order screen, enter your email address and make up a password. You have to agree to automatic rebilling before the Subscribe Now button activates. Press the button to start your subscription.
- Check your Inbox for a verification email. Click on the Confirm Email button in the email. A confirmation Web page will open up that contains a download link for the app. Click on the Download Software button.
- Open the downloaded file to run the installer. Click on the Install button and then accept the Windows user access control challenge. The installer completes very quickly. Click on Run to open the app.
- Get the Android app from Google Play and the iOS app from the Apple App Store for iPhones and iPads.
- When the app opens, log in with your email address and the password you set up. The desktop app shows a map of the world.
- Double-click on a country marker to get connected or press the Connect button to start the VPN with the fastest server.
- Click on the marker symbol in the left strip of the app to get a list of servers.rn
- The list shows the current connection speed to each server from your location.
FAQs
Is IPVanish VPN free?
IPVanish is not free. However, if you take out the one-year plan and then cancel before 30 days have passed, you get all your money back.
How much does IPVanish cost?
The price per month for an IPVanish subscription is £10.99. Taking out a longer subscription brings down the price per month with quarterly and yearly plans available.
Can IPVanish unblock Netflix?
IPVanish dodges the location detection system of Netflix with its servers in the USA, the UK, Australia, and Japan.
Are some IPVanish servers faster?
IPVanish constantly tests the speed of connections to each of its servers from your device and shows this in the app. So, when you make your selection, you can see which server will give you the best service.
Does IPVanish work with Amazon Prime?
IPVanish works with Amazon Prime but only with some of its servers. You have to try out different servers to discover one that works because the best server options for Amazon Prime Video are not flagged.
The verdict on IPVanish
IPVanish is one of the top VPN services in the world. Its ability to get into the US Netflix library from anywhere is a great feature. You need high download speeds for video streaming to prevent buffering, so the poor speed performance of IPVanish was disappointing.
Watch out for the tricky pricing, though, and remember that you only get the 30-day money-back guarantee with the one-year plan. You will probably want to look into other VPNs before you settle on your preferred system and actually take out a subscription. The best VPNs you should consider as alternatives to IPVanish are ExpressVPN and NordVPN, which offer better speeds and can also get cross-border access to Netflix.





