Hotspot Shield VPN Review (2024)
Hotspot Shield has been operating since 2005. The VPN provider has gone through a lot of changes over the years, including a number of changes in ownership. However, these moves have provided to be beneficial to the VPN system and we shall cover these upgrades in this VPN review.
What we like
- A strong VPN server location list that includes some repressive countries
- Split tunneling (called smart VPN)
- Automatic WiFi protection option
- Good performance unblocking streaming services
- 7-day free trial
- 45-day money-back guarantee is very generous
What we don't like
- Simultaneous connection allowance of five devices is not very high
- Had some data disclosure problems in the past
- Has a poor record on privacy
- Split tunneling is not available in all Hotspot Shield apps
- Complicated corporate history
- Adverts in the free version
Features
| Hotspot Shield Features | |
|---|---|
| Rating: | 4/5 |
| Price: | $7.99 – $12.99 per month |
| Refund period: | 30 days |
| Based in which country: | Switzerland |
| # devices per license: | 10 |
| # servers: | 1,800 |
| Server locations: | 127 locations in 85 countries including the USA, Canada, the UK, Australia, New Zealand, Japan, France, and Germany |
| Streaming sites unblocked: | Netflix, BBC iPlayer, and NBC |
| Supports torrenting: | Yes |
| Does VPN keep logs: | No |
| 24/7 customer support: | Yes |
| Website: | https://www.hotspotshield.com/ |
Hotspot Shield was created by AnchorFree, Inc. In 2005. While remaining at the same base in Redwood City, California, the company changed its name to Pango Group in 2019. The company charged its EU customers through a division called AnchorFree GmbH and changed that company’s name to Pango GmbH at the same time. However, a UK division, called AnchorFree Ltd, still operates under the same name.
Pango renamed Hotspot Shield to Pango Hotspot Shield and bundled it with the VPN’s other privacy services. This package included Robo Shield (another Pango asset), a call blocker for automated dialer sales calls, 1password password manager, and Identity Guard identity protection. However, this bundle has now been dropped under the Hotspot Shield name and is now marketed as Aura.
In July 2020, Pango was bought by Aura, the owner of Identity Guard. Pango’s other assets include Identity Defense, a rival of Identity Guard, which Aura still owns as a separate division. Aura moved its Intrusta antivirus/malware protection package into Pango. Aura also owns Touch VPN and identity protection brands PrivacyMate and FigLeaf.
Pango Group also owns Ultra VPN, VPN 360, and Betternet VPN. In October 2021, the company acquired the Comparitech tech review website, which is heavily based on VPN reviews, through its AnchorFree Ltd subsidiary. The UK company bought another VPN review website called ProPrivacy in February 2022.
Confusingly, Aura, in turn, is a brand owned by Intersections, Inc, and it is this company name that appears as the copyright owner on the Hotspot Shield website. In the Hotspot Shield, such as the Terms of Service, that company name is expressed as Intersections LLC doing business as Aura. The VPN Privacy Policy mentions Intersections LLC doing business as Pango. Intersections, Inc is owned by WC SACD One Parent, Inc, which is owned jointly between WndrCo, General Catalyst, and iSubscribed.
Privacy and security
Hotspot Shield hasn’t done too well in the past, and its earlier data indiscretions still haunt the brand name.
A study by the Commonwealth Scientific and Industrial Research Organization (CSIRO) in August 2016 found that Hotspot Shield hijacked some of the URLs that it processed to place its own affiliate code on visits to some retail websites, including Best Buy, Target, eBay, Alibaba, Overstock.com, NewEgg and Macy’s.
The study found that the VPN system included five tracking libraries in its code. The app also injected its own adverts into the websites that it forwarded to the browsers of its users. The CSIRO rankings of the worst VPNs for privacy put AnchorFree’s other VPN service, Betternet, as the third worst in the world. The top two immediately folded, leaving Betternet with the crown.
In August 2017, the Center for Democracy and Technology reported the Hotspot Shield Free VPN to the Federal Trade Commission in the USA for undisclosed sharing of user data with advertisers.
In 2018, it was discovered that the app leaked location information.
Hotspot Shield’s Terms of Service state that it still injects advertising into the web pages that it processes in the free version of the service but declares that it does not do this in the paid version.
Legal protection
For legal matters, Hotspot Shield’s location is the state of Virginia in the USA. This isn’t one of the best locations for legal domicile because the US government agencies are known to lean on VPNs to get them to comply with activity tracking.
The US location also makes the service vulnerable to attack by US copyright lawyers, which is an important factor for those who engage in P2P file sharing networks. The crucial factor in this issue is whether the service retains activity logs. This is because if records exist, copyright lawyers can seize them and use connection records from the VPN to track the activity of an individual from a Web source back to an internet service provider. ISPs are legally obliged to store the activity records of their customers.
The tracking of an individual’s online activity involves looking for the identifier of that person’s device on internet-related records. That identifier is called the IP address.
For many years, Hotspot Shield stated in its privacy policies that the IP address was not regarded as personally identifiable information (PII). This raised concerns among internet privacy activists because it enabled the business to store information indexed by IP address while still maintaining that it protected the privacy of its customers. Activity linked to an IP address is exactly the type of data that copyright lawyers and law enforcement agencies look for. However, Hotspot Shield has altered this stance and now includes the IP address as part of its definition of PII. This gives its privacy policy more strength.
Network address translation
There are two strands of protection that VPNs offer, and they mask the identities and activities of the VPN’s customers. The first of these services is an IP address substitution. There are a few ways that this can be implemented, and Hotspot Shield does it through shared IP addresses.
Each VPN server holds a pool of IP addresses. When a customer connects to the service, the VPN server allocates one of its IP addresses to that VPN connection. No matter where the applications on the protected device what to contact, the VPN app on the device directs all traffic to the VPN server.
All traffic on the internet is broken up into sections, and the structure that carries each chunk is called a packet. The packet has a header that contains the source and destination IP address of the packet. When a VPN connection is in place, the VPN server receives all packets from a customer and forward’s them to its intended destination – which is usually a Web server. The VPN server changes the source IP address in the packet header to the address that it allocated to that customer for the session. When the recipient replies to the request, it uses that source IP address or the destination of the response, and so that reply goes to the VPN server.
The incoming packet needs to be forwarded to the right customer because the VPN server can be working for many customers at the same time. So, the VPN system maintains a lookup table that contains the real IP address and the substituted IP address of each customer. The server is then able to forward the received reply to the right customer. This cross-reference is called network address translation (NAT).
When each customer ends the VPN connection, the cross-reference record for that session is removed from the NAT table, and the representative IP address is returned to the pool for use by another customer.
Activity logging
Activity logs are created at the end of the VPN session if the VPN server archives off the NAT table line for the session before it deletes it. This line contains the IP address of the customer, the substituted IP address, a timestamp of the start of the session, and a timestamp of the end of the session. This is all a copyright lawyer needs to trace the activities of an individual and start legal proceedings for illegal downloads of copyrighted entertainment.
This is why it is important to know whether the VPN stores IP addresses. Despite Hotspot Shield’s past legal dodge of not defining the IP address as personal data, the company no longer avoids this disclosure. The logging policy of Hotspot Shield states that it does not retain user data. So, customers of the service can now be assured that their internet connections are anonymized.
There is a lot of suspicion about Hotspot Shield because of its past behavior. However, the business has cleaned up its act, and now its activity logging practices are no better or worse than most of the popular VPN services.
Hotspot Shield VPN protocols
While IP address switching is one strand of a VPN’s functionality, the other part of a VPN’s work is the protection of an internet connection. This occurs between the customer’s device and the VPN server, and it is implemented through a set of procedures called a protocol. There are a number of VPN protocols in existence, but AnchorFree decided to make up its own, called Hydra. There is no information on how this protocol works, but the company claims that it is almost two and a half times faster than OpenVPN, which is the leading VPN protocol.
Hydra was originally called Catapult Hydra, but they shortened the name. The little information that can be gleaned about this system is that it is very similar to OpenVPN. This uses a two-phase approach to encryption this is because the main encryption cipher used for the session is a symmetric key system. That means the same key is used to encrypt and decrypt a message. The problem with that scenario is that one side needs to send the key to the other.
An encryption cipher is a formula with one value missing. The key is that missing number. Changing the key completely alters the outcome of the encryption transformation, so it is necessary to have the key in order to reverse the transformation.
Hotspot Shield uses the Advanced Encryption Standard (AES) for its encryption cipher. The length of the key decides the strength of the key’s protection because a longer key would take more time to guess. Hotspot Shield uses a 256-bit key for its AES encryption. This is expressed as AES-256. A 256-bit key is impossible to crack.
A problem with Hydra is that it is a proprietary system and so its processes are kept secret. Most other VPN protocols, such as OpenVPN, and WireGuard are open-source, so its choice of encryption services is widely known. The logic behind this is that knowing the formula does a hacker no good without also knowing the key.
As an alternative protocol, Hotspot Shield provides the IKEv2/IPsec combination. This is a low-level VPN protocol (IPsec) that is so close to networking processes that it doesn’t have the functionality to manage encryption keys. So, IKEv2 is used for this purpose. IKEv2/IPsec is a very efficient combination, and it is often used for mobile devices because it places less load on the device’s battery.
Hotspot Shield DNS leak protection
The VPN server is a type of service that is called a proxy. It stands in for your computer when your internet traffic goes out to a Web server. As explained above, the VPN puts a different IP address in the header of the packets that it sends out, so no one knows that it is you accessing those systems. However, the VPN service needs to get your traffic to the VPN server.
The Hotspot Shield app that you download onto your device acts as an agent. You select a VPN server to connect to, and then the client creates a “tunnel” to that server. The tunnel is formed through an authentication process that uses a public key encryption system.
With public key encryption, a key pair is calculated. These are an encryption key and a decryption key. The two are related but different. You can’t guess the decryption key if you know the encryption key, and you can’t decrypt a text with the encryption key. Thus, the encryption key can be made public as long as the decryption key is kept private.
The VPN app uses the public key of the server to encrypt a challenge. If the reply comes back correct, the server has proved its identity because it holds the related decryption key. The server uses the client’s public keys in its replies over the internet connection. This enables it to securely transmit the AES encryption key. After this, both sides use the AES cipher to encrypt traffic, and this is the tunnel.
The VPN app intercepts all traffic leaving the device and cloaks it by encrypting the packets entirely. This includes encrypting the packet headers. Routers on the internet need to read the headers so they can see the destination IP address. The VPN app puts the entirely encrypted packet inside another packet and addresses that outer packet to the VPN server.
The VPN server extracts the inner packet and decrypts it, revealing the true destination address in its header. It then puts in the substitute IP address in the source address field and sends it on its way. Replies are encrypted and sent back to the VPN app. This decrypts the inner packet and passes it to the application that sent out the original request.
Hotspot Shield IP leak protection
The benefit of the tunnel is that it prevents your internet service provider from logging your online activities. This record of all of your internet connections is the final step in the activity tracking trail that copyright lawyers need to sue torrenters. It is also used by government law enforcement agencies. The tunnel means that your ISP only sees traffic going back and forth to the VPN server. They have no way to know which systems you are actually connecting to.
Unfortunately, if your VPN connection drops, all subsequent traffic will be unprotected, and your ISP will start logging your internet activity. This is called an IP leak because it discloses the IP addresses of the servers to which you connect.
The Hotspot Shield VPN app has a feature that prevents IP leaks. This is called the Kill Switch. If this option is turned on, the VPN takes control of all internet access. Traffic can only travel through the tunnel, and if the VPN connection is broken, you lose the internet. This mechanism ensures that you notice that the VPN connection has been lost and turn the service back on again.
Hotspot Shield DNS leak protection
The web addresses that you see in the address bar of your browser mean nothing on the internet. Routers only deal with IP addresses, so your browser has to get that address before it can request a Web page.
The cross-reference between Web addresses and internet addresses is held in the Domain Name Service (DNS). This is a very large database, and it is held in sections that are distributed around the world. To speed up DNS queries, your ISP runs a service called a DNS resolver.
The DNS resolver handles requests and stores the most recently requested IP addresses. Although this is a great service for speed, it compromises our internet privacy and freedom. The ISP can use this mechanism to block access to websites simply by maintaining a cross-reference that points to the wrong page – such as an error page on the ISP’s server. The DNS query also gives your ISP another opportunity to log your activities. The disclosure of a DNS query is called a DNS leak.
Hotspot Shield protects DNS queries with encryption. One difference between Hotspot Shield and other VPMN services, such as CyberGhost and Surfshark, is that, according to the Hotspot Shield support pages, DNS queries don’t travel down the tunnel. However, they are encrypted and so cannot be blocked or logged by your ISP.
Hotspot Shield virtual locations
Hotspot Shield uses cloudy terminology when it refers to the locations of its VPN servers. It refers to them as “virtual locations.” This is confusing because the term can have two different meanings.
A major reason to use a VPN is to spoof your location. All IP addresses can be traced to a physical location, and so by connecting to a VPN service in another country, such as France, the Web servers you contact will think that you are there. His can be said to be a virtual location – it is not your real location.
However, VPNs can perform this location-shifting trick in two ways. The usual way is to operate a server in a specific location, so when you click on Paris, France, as a location, your VPN app connects to a server that is actually located in Paris. So, no matter whether you really are, it seems to Web servers that you are in Paris – that is your virtual (not real) location.
Another meaning of “virtual location” is that the VPN server is not actually where it is said to be – the server is in that virtual location but really somewhere else. The VPN company buys a list of IP addresses that are “known” to be in Paris but loads them onto their server in Chicago in the USA. All of the VPN apps used by the VPN system are then set up to connect to the Chicago server whenever the user clicks on Paris, France.
Although Hotspot Shield names 85 countries in its server location list, a little digging reveals that only 20 of them are real – all the rest are virtual server locations.
The use of virtual locations is widespread in the VPN industry. However, most VPN services, such as ExpressVPN and NordVPN, make it clear in their server lists which are real and which are virtual. This practice is particularly widespread for providing server locations in India, Russia, and China where VPN server operators are either obliged to implement activity logging or they are completely illegal. Virtualizing these locations and operating them from servers in safer countries dodges national laws that could render the use of the VPN a waste of time.
Website blocking
That location switching trick that VPN servers perform can get around the access blocking processes of many websites. Many news sites, gambling sites, and game servers present different content to people in different locations. In some cases, they restrict access to people who are physically located in one specific country. Location detection is particularly prevalent with streaming services.
Not every VPN can get around the location checks of all video streaming services, so the quality of a VPN comes down to its location spoofing capabilities. We tested Hotspot Shield to see whether it could get cross-border access to some of the most important video sites. Here are the results:
| Service | Test |
|---|---|
| Netflix | Tested for the USA, the UK, France, Norway, and Japan: it worked for all |
| Disney+ | Worked for the USA but not for the UK, France, Norway, or Japan |
| BBC iPlayer | Yes |
| ITV Hub | Yes |
| Channel 4 | Yes |
| ABC | No |
| NBC | Yes |
Pricing
Hotspot Shield offers three editions:
- Basic
- Premium
- Premium Family
The Basic edition is free to use but only offers one server location, which is in the USA.
The Premium edition is the full Hotspot Shield service and allows five simultaneous connections. That means you can install the app on as many devices as you like, but you can only have five of them connected to the service at any one time.
The Premium Family edition is a multiple license deal that gives you five Premium licenses, which allows a total of 25 simultaneous connections (5 x 5). Each edition is offered in two payment plans: a month-to-month payment plan and a one-year plan.
The prices for the two paid editions are:
- Premium: $12.99 per month, $95.99 per year ($7.99 per month)
- Premium Family: $19.99 per month, $143.88 per year ($11.99 per month)
All plans include a 45-day money-back guarantee.
You can pay for your subscription with a credit card (Visa, Mastercard, American Express, Diners Club, JCB, or Discover) or PayPal. There is no option to pay with cryptocurrency. You can buy the service through a mobile app, getting the android app from Google Play or the iOS app from the Apple App Store. However, Hotspot Shield doesn’t accept Google Play or Apple Pay.
You can get a 7-day free trial of the Premium edition. However, this version will roll on to the monthly payment plan at the end of the trial period. If you do want to commit to using the Hotspot Shield VPN long-term, you would be better off taking out the one-year plan. So, whether or not you intend to continue using Hotspot Shield, cancel the service before the free trial expires.
How to install
1. Access the 7-day free trial of Hotspot Shield. Fill in your email address and credit card details. You have to commit to a purchase before you start the trial. However, you are free to cancel the service before the seven days expire, and then you won’t be charged.

2. After clearing this page, enter a password to set up your account.
You now get access to the Download page.

3. Click on the Hotspot Shield VPN Get button to download the installer. Click on the Download button on the next screen. Run the installer when the download completes and click through the installation screens.
Once the installation completes, it will flick through a list of service highlights. Then you get to the main screen of the VPN. The app opens with your credentials already plugged in, so you don’t need to sign in.
The main screen shows your data throughput for the day and the last place that you connected to. By default, the app will connect automatically to that last accessed server.

4. Clicking on the arrowhead in the Virtual location box brings up the list of available server locations.

5. The server list shows the countries in which Hotspot Shield has servers, and there are multiple server locations in some countries. Click on the box for a country to get down to city level.

6. A Connect link appears when the mouse pointer is over a server location. Click on this link to get the VPN to connect to the location.
When a VPN connection has been established, the main screen of the VPN app shows a great deal of information.

7. The first panel on the main screen shows a map of the world with the currently connected VPN location indicated on it. You can change this location at any time by clicking on the arrowhead next to the current location name.
In the lower-left panel, the Latency number shows the Roundtrip Time as reported by Ping.
8. Click on the bolt symbol, which is at the bottom of the menu strip on the left of the screen, to get to the settings menu. Click on the Protocols tab to see the VPN protocol options.

9. Go to the Advanced tab to find the Kill Switch option. Turning this on will prevent internet traffic without the VPN being turned on. This service will only work if the VPN app is open. You can get the VPN app to open automatically when the operating system starts up by going to the General tab and turning on the Start on Launch option.

10. Click on the house symbol at the top of the menu strip to get back to the main screen of the app. Click on the blue button at the bottom of the screen to disconnect the VPN.
Speed tests
The VPN app display includes its own speed report. However, we didn’t rely on that for our connection speed test. These tests were performed with Meter.net. Tests were carried out while connected to the Three networks in the UK and with the VPN protocol in the app set to Hydra. Each test was performed three times, with the middle result taken for the report.
First, to establish a performance baseline, we tested a connection to a nearby server without the VPN turned on:

The download speed shown was 10.47 Mbps, and the upload speed was 2.89 Mbps. Using the generic United Kingdom server location, we performed the speed test, connecting to the same test server used for the unprotected speed test. The results were:

At 11.60 Mbps, the download speed on the protected connection was slightly better than the connection speed without the VPN. The upload speed was slightly lower at 2.22 Mbps.
Long-distance connections across the internet are slower because packets have further to travel and pass through more routers – this test, without the VPN, turned on, went to Sydney, Australia:

As can be seen, a connection to the other side of the globe was much slower than a local connection. The connection had a download speed of 2.00 Mbps and an upload speed of 0.17 Mbps.
Turning on the Hotspot Shield service, using the London VPN server, we connected to the same test server in Sydney again.
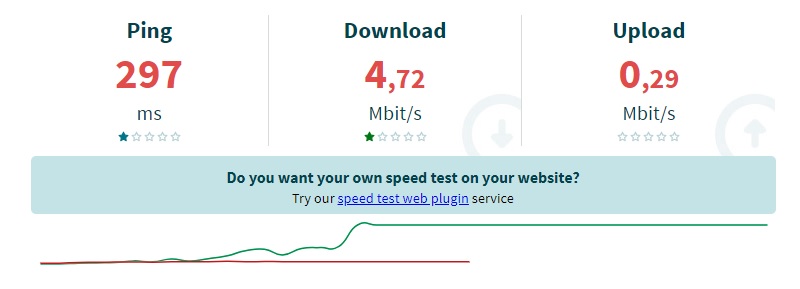
The VPN improved both the mean download speed, which more than doubled to 4.72 Mbps, and the mean upload speed, which was 0.29 Mbps.
It might seem hard to believe that a VPN can improve speeds on an internet connection – the service performs encryption on each packet, which should always slow transfer speeds. However, telecommunications businesses sign agreements with counterparts in other parts of the world to carry traffic and those contracts can include conditions, such as speed limits that lower the price of the service. So, the results seen in these tests are possible because it shows that Hotspot Shield has better peering agreements with long-distance carriers than the ISP for these tests.
FAQs
Does Hotspot Shield work in China?
Hotspot Shield works in China to provide access to websites and internet services outside the country. The VPN service also has virtual servers that operate with Chinese IP addresses. That means users outside China can get access to websites that only serve national visitors, such as Chinese TV station video streaming services.
Can I use Hotspot Shield for torrenting?
Hotspot Shield is a good option for torrenting. This is because the service offers fast speeds and unlimited bandwidth. The company had some problems with logging issues in the past, which makes some analysts nervous about recommending this VPN system. However, Hotspot Shield has now changed its logging policy, which means that it does not lay a paper trail for copyright lawyers to grab.
Is Hotspot Shield a fast VPN?
The speed you get from Hotspot Shield depends on the underlying performance of your regular internet service and the destination of your internet connection. The system increases the speed on most connections, with the amplification increasing with greater distances.
Is Hotspot Shield a firewall?
Hotspot Shield operates a system called network address translation (NAT). When implemented on home routers, this mechanism is often referred to as a NAT firewall. The service blocks incoming connections and confounds hacker research attempts to discover the address of the devices protected by the VPN. The service will also absorb DDoS attacks, which are floods of malformed connection requests – the VPN only passes valid data packets back to the protected device.
Does Hotspot Shield block infected files?
Hotspot Shield is a privacy service, and it does not examine the contents of the packets that it passes back to the devices that it protects. This means that there is no mechanism in the service to assess files for infection. You should install an antivirus system as well as run the Hotspot Shield VPN service.
To sum it up
Hotspot Shield has had some problems in the past. However, after sorting out its treatment of IP addresses and eradicating activity logging, this tool is safe to use for a variety of online activities, such as torrenting, gaming and getting cross-border access to geo-restricted video streaming services.
Hotspot Shield claims to be the fastest VPN on the market. It’s difficult to validate that status because it would need to be tested for connections from every location in the world through each of the Hotspot Shield servers. However, in our tests, Hotspot Shield performed very well and actually increase connection speeds.
Hotspot Shield offers good value for money, and we rank the service up in the top five alongside ExpressVPN, NordVPN, Surfshark, and IPVanish.