Cryptostorm VPN Review (2024)
Cryptostorm anonymizes your purchase by generating a cryptographic network access token you use to authenticate yourself in the network. It also provides a custom OpenVPN version that eliminates the logging of your IP and DNS. It’s also open-source.
What we like
- Torrent-friendly
- Accepts Bitcoin
- Intuitive Windows widget
- Availability of a custom patch for OpenVPN
- Token-based
- Zero-logs
- Strong security
- Strong stance on privacy
What we don't like
- No streaming
- No widget for platforms other than Windows
- No live support
- Website and resources difficult to navigate
- Jargon-heavy guides
- Allegedly owned by Douglas Spink, convicted drug smuggler, and active zoophile
- There is a chance it might be an FBI honeypot
Features
Cryptostorm is an Iceland-based veteran of the VPN arena with offices in Canada. Previously known as Cryptocloud, the provider aims to take VPN a step further than location spoofing.
The fact that Cryptostorm is token-based brings a bundle of advantages. First of all, there are no accounts, passwords, and usernames. Also, your token does not begin “eroding” until your first authentication and use of the VPN. It means you can buy a token and keep it until you need it.
At the same time, you shouldn’t lose it because the provider would not be able to replace or reproduce it – they delete records of sold tokens.
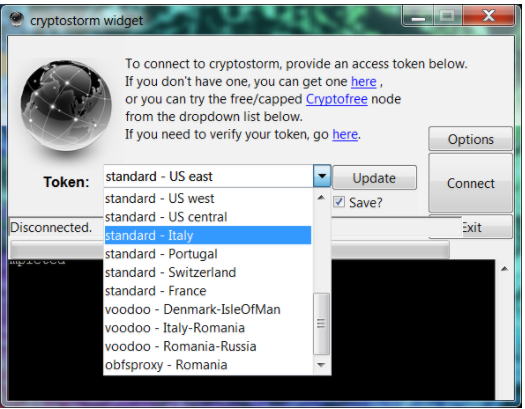
Windows users can use Cryptostorm via a nifty desktop widget, which is a nice little program with minimal settings but excellent performance. It does require your token whenever you connect to a server for the first time.
Mac OS, iOS, Android, and Linux users will have to make do with the OpenVPN program plus the Cryptostorm configuration files.
There is no support other than through email, FAQs, and forums, but you could use the IRC chat to seek some help from other users if you need a helping hand quickly.
Overall, usability is smooth for a Windows user and average for everyone else. What I disliked, however, was the provider’s website, forum, and GitHub repository. The downloads are so dispersed across multiple pages you can never find anything in one place. The website has a hideous design and font that do not help comprehend the technical aspects from the get-go.
Cryptostorm is not a hassle to use, but its website is difficult to navigate. And it hurts my eyes. I’m willing to ignore the poor website organization due to several factors – a) obviously, the developers focus on the VPN performance rather than the website’s compartmentalization, b) tastes differ, c) a lot of work has been put into the website, forum, and the GitHub repositories.
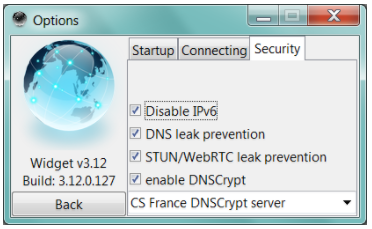
The Windows widget – although tiny – bundles a bag of goodies. You have toggles to disable IPv6, DNS leak prevention, STUN/WebRTC leak prevention, and DNSCrypt server choice. The latter routes your traffic through two servers, making it nearly impossible for targeted surveillance to identify your real location.
You can also customize ports and protocol (UDP, TCP) and the timeout, and define how the program starts and connects.
Since the provider keeps no logs and knows no identities, you can torrent, stream, and play. I couldn’t find any information regarding simultaneous connections, however.
Pricing
Cryptostorm accepts a variety of payment methods – PayPal, credit cards, Stripe, and Bitcoin. Their roster of paid plans is flexible enough to make up for the lack of a free trial. $1.86 buys you a week of Cryptostorm while you can have a month of it for $6, which is a modest price by modern standards.
Their three-month plan kicks in at $16, six-month at $28, one-year at $52, and two-year at $94. It also offers custom bundles – 5 x one-month tokens will set you off $24, 11 tokens – $48, and 25 tokens – $97, which is a feasible solution for teams.
As I mentioned, Cryptostorm is a token-based VPN. It means the provider does not directly sell its subscriptions. Instead, it redirects you to one of its vendors. After the checkout, you get an email with your unique token and an all-in-one introduction to the service, complete with useful information and links.
The service doesn’t offer any money-back guarantee. The closest thing to a refund policy implies the provider should shut you off for some violation of their ToS. That would make you eligible for a partial refund.
All paid plans come with the same number of servers, and support for multiple operating systems. There’s no live support; you need to rely on their forum and guides.
Tests
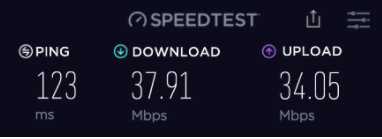
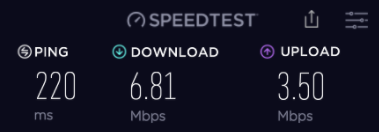
Cryptostorm is not the speediest network but it delivers. With my pre-VPN speed being somewhere at 40Mbps for download and 35Mbps for uploads, most of Cryptostorm’s servers went down to 7Mbps for downloads regardless of server proximity, while the upload speeds varied greatly.
Here is my speed test before connecting to the VPN:
Their US, Dallas server:
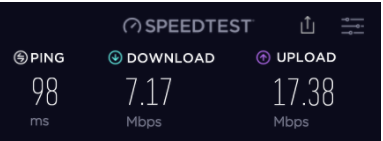
Phoenix server:
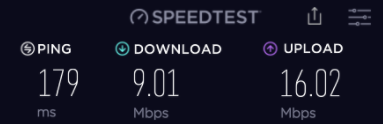
Coventry, UK:
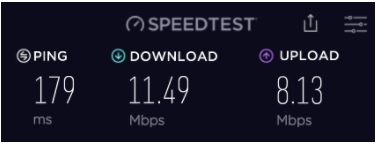
Bucharest, Romania Obfsproxy connection:
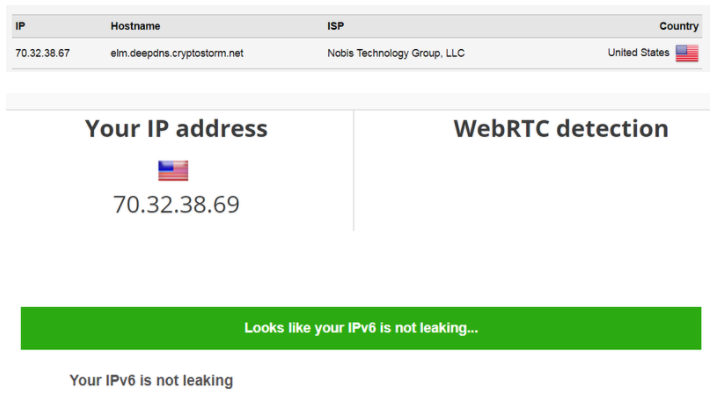
Cryptostorm passed my security tests with flying colors – no DNS, WebRTC, or IPv6 leaks:
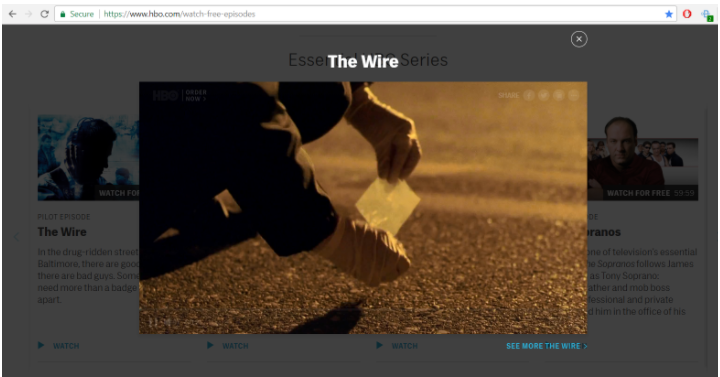
As much as a tried changing my connection settings, deleting cache, and all that jazz, Cryptostorm only got me as far as to HBO:
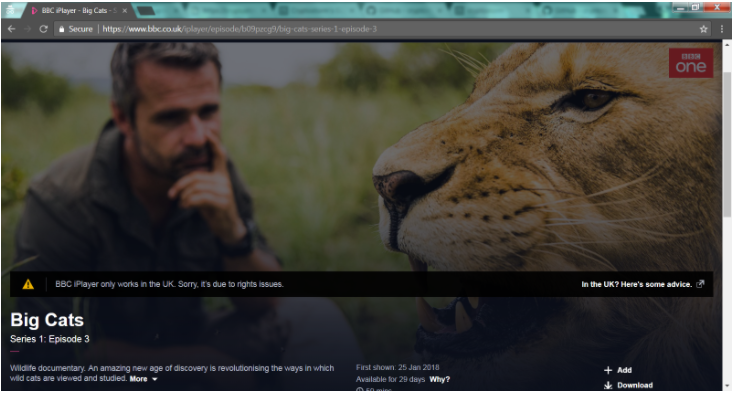
It failed to unblock Netflix US or BBC iPlayer. Netflix recognized a VPN while BBC iPlayer knew I wasn’t coming from the UK:
Privacy and security
Cryptostorm relies on OpenVPN and 256-bit encryption backed by RSA-2048 asymmetric key and SHA-512 hash authentication. Don’t worry if it sounds like gibberish – the security is top-notch by today’s standards.
If you know some tech speak, their OpenVPN patch is set to /dev/null and your private IPs won’t show up in the temporary status logs. The sheer fact that the provider doesn’t bother to include weak protocols with known vulnerabilities (PPTP et al) speaks volumes about their work ethic. The provider does not know your identity. Nor does it keep your token. It keeps no logs. It’s also open-source and decentralized.
Open-source means the source code is available for everyone to audit. This is good. It helps the developers identify and patch flaws fast while it helps tech-savvy nerds verify that the VPN is as secure as it claims it is. Decentralized means the company is sort of Iceland-based but has offices in Canada and other locations. But there is no headquarters. This affords the team a degree of operational flexibility but also makes it difficult to pinpoint a jurisdiction. The company has a Privacy Seppuku Pledge page, which gives a sneak peek at its history and stance on privacy. Cryptostorm also offers Privacy Policy and ToS pages – brief and devoid of mind-numbing legalese.
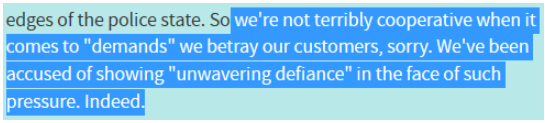
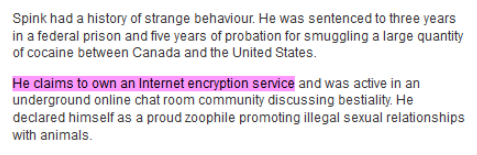
Having reviewed my share of VPNs, however, I developed a reasonable paranoia with regard to VPN providers. Although things look bright on the surface here, I couldn’t help but try to dig some dirt. For what it’s worth, there were allegations of Cryptostorm being an FBI honeypot in the past. The allegations referenced an unconfirmed owner of Cryptostorm, Douglas Spink (drug smuggling, bestiality farm, multiple convictions). Case in point – Spink was convicted of smuggling $34 million worth of cocaine in 2005, and released after 3 years of a total 17-year sentence. This led some to believe Spink cooperated with the FBI. Also, the company refuses to acknowledge or explain its legal compliance with the Canadian data retention laws.
In being completely honest, Cryptostorm doesn’t look nearly as ethical now as it first seemed when I started reviewing it. The allegations first date back to 2013, but the recent mention of Spink owning an Internet encryption service date back to 2016, which isn’t that distant of a past. I’m surprised the service never bothered to address these concerns.
Final thoughts
I have mixed feelings about Cryptostorm. It’s unique, anonymous, decentralized, affordable and robust on the one hand, but it could also be a perfect NSA or FBI honeypot. The team behind the VPN need to do something to disavow the allegations that have been circulating the web for years now. The fact that they don’t – and remain anonymous – doesn’t make them look any more trustworthy.




